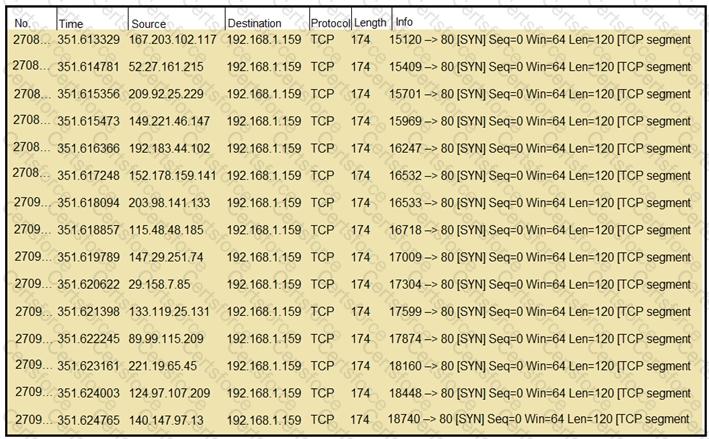
In the provided Wireshark capture, we see multiple TCP SYN packets being sent from different source IP addresses to the same destination IP address(192.168.1.159:80)within a short time window. These SYN packets do not show a corresponding SYN-ACK or ACK response, indicating that these TCP connection requests are not being completed.
This pattern is indicative of aSYN flood attack, a type of Denial of Service (DoS) attack. In this attack, a malicious actor floods the target system with a high volume of TCP SYN requests, leaving the target's TCP connection queue (backlog) filled with half-open connections. This can exhaust system resources, causing legitimate connection requests to be denied or delayed.
Thecountermeasurefor this scenario, as highlighted in theCyberOps Technologies (CBRFIR) 300-215 study guideunderNetwork-Based Attacks and TCP SYN Flood Attacks, involves:
Increasing the backlog queue: This allows the server to hold more half-open connections.
Recycling the oldest half-open connections: This ensures that legitimate connections have a chance to be established if the backlog fills up.
[Reference:CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter 5: Identifying Attack Methods, SYN Flood Attack section, page 146-148., , , , ]
Submit