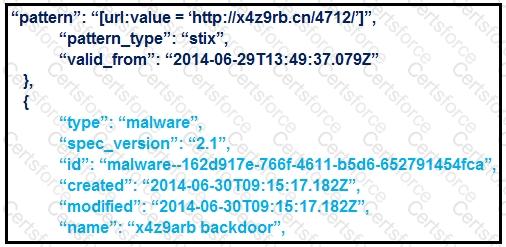
This STIX (Structured Threat Information eXpression) JSON snippet provides two key elements relevant for IOC (Indicator of Compromise) analysis:
The indicator pattern shows a suspicious URL:→ "pattern": "[url:value = 'http://x4z9rb.cn/4712/']" This is the actual IOC that can be used for detection.
The type of object that the indicator relates to:→ "type": "malware"→ "name": "x4z9arb backdoor"This indicates the nature of the threat associated with the IOC is malware.
Therefore, the threat is "malware" and the associated indicator (IOC) is the URL: http://x4z9rb.cn/4712/
Option A correctly captures both the IOC category ("malware") and the indicator value ("http://x4z9rb.cn/4712/").
[Reference:CyberOps Technologies (CBRFIR) 300-215 study guide, Chapter on “Understanding Threat Intelligence Platforms,” including the use of STIX/TAXII for representing threat data., ]
Submit