An architect is working on the data protection design for a VMware Cloud Foundation (VCF) solution. The solution consists of a single Workload Domain that has vSphere Supervisor activated. During a customer workshop, the customer requested thatvSphere Podsmust be used for a number of third-party applications that have to be protected via backup.
Which backup method or tool should be proposed by the architect to satisfy this requirement?
A cloud operations team is managing multiple Supervisor Clusters across two regions. Each region hosts its own vSphere Kubernetes clusters, integrated through a federated service mesh to enable consistent service connectivity and policy enforcement across environments.
The application team wants to expose a multi-tier microservice named “GovApp”, which includes front-end, API, and database services distributed between the two regions. Uniform traffic routing, identity, and security policies are also needed for these workloads regardless of the cluster or region in which they are deployed.
To meet these requirements, the architects decide to create a Global Namespace that spans both Supervisor Clusters.
Which two statements describe the requirements for a Global Namespace in a vSphere Kubernetes Service Mesh deployment? (Choose two.)
What is the function ofContourin a VMware vSphere Kubernetes Service (VKS) cluster?
An administrator enabled cluster scaling by running kubectl edit deployment and updating the number of replicas from 5 to 10. When the cluster was redeployed with the number of replicas set to 5, what was the result?
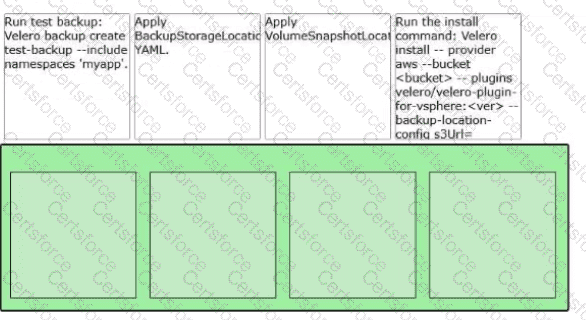
A VMware Administrator is tasked with implementing a backup and restore strategy using Velero and external object storage for the namespace 'myapp1. Arrange the steps In the correct order of operations to enable Vetero.
An administrator is modernizing the internal HR and payroll applications using vSphere Kubernetes Service (VKS). The applications are composed of multiple microservices deployed across Kubernetes clusters, fronted by Ingress controllers that route user traffic through Avi Kubernetes Operator. During testing, it is discovered that manually creating and renewing TLS certificates for each Ingress resource is error-prone and leads to periodic outages when certificates expire. The requirements also mandate that all application endpoints use trusted certificates issued through the corporate certificate authority (CA) with automatic renewal and rotation.
Which requirement can be met by using cert-manager?
A company standardized on the following configurations:
• vSphere Kubernetes Service (VKS) upgrade is separate from vCenter upgrades.
• A private registry will be utilized.
How should an administrator adhere to these standards?
An administrator is configuring the Supervisor Service in vCenter.
Click the option an administrator uses to begin creating a vSphere Supervisor Zone.

A VMware vSphere Kubernetes Service (VKS) cluster exposes three layers of controllers to manage its lifecycle. Which set identifies these layers?
What are three benefits of VMware vSphere Kubernetes Service (VKS)? (Choose three.)