Which setting can an administrator configure in the LiveUpdate policy?
An administrator is unknowingly trying to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client’s system.
Drag and drop the technologies to the right side of the screen in the sequence necessary to block or detect the malicious file.

An administrator is unable to delete a location.
What is the likely cause?
An organization has several remote location with minimum bandwidth and would like to use a content distribution method that does NOT involve configuring as internal LiveUpdate server.
What content distribution method should be utilized?
An administrator is responsible for the Symantec Endpoint Protection architecture of a large, multi-national company with three regionalized data centers. The administrator needs to collect data from clients; however, the collected data must stay in the local regional data center. Communication between the regional data centers is allowed 20 hours a day.
How should the administrator architect this organization?
Refer to the exhibit.
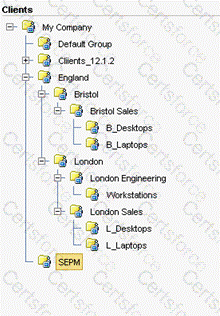
A manufacturing company runs three shifts at their Bristol Sales office. These employees currently share desktops in the B_Desktops group. The administrators need to apply different policies/configurations for each shift.
Which step should the administrator take in order to implement shift policies after switching the clients to user mode?
An administrator needs to configure Secure Socket Layer (SSL) communication for clients. In the httpd.conf file, located on the Symantec Endpoint Protection Manager (SEPM), the administrator removes the hashmark (#) from the text string displayed below.
#Include conf/ssl/sslForcClients.conf<
Which two tasks must the administrator perform to complete the SSL configuration? (Select two.)
Which package type should an administrator use to reduce a SEP environment’s footprint when considering that new SEP 14 clients will be installed on point of sale terminals?
An administrator plans to implement a multi-site Symantec Endpoint Protection (SEP) deployment. The administrator needs to determine whether replication is viable without needing to make network firewall changes or change defaults in SEP.
Which port should the administrator verify is open on the path of communication between the two proposed sites?
An administrator changes the Virus and Spyware Protection policy for a specific group that disables Auto-Protect. The administrator assigns the policy and the client systems apply the corresponding policy serial number. Upon visual inspection of a physical client system, the policy serial number is correct. However, Auto-Protect is still enabled on the client system.
Which action should the administrator take to ensure that the desired setting is in place on the client?