A Symantec Endpoint Protection administrator must block traffic from an attacking computer for a specific time period.
Where should the administrator adjust the time to block the attacking computer?
An organization recently experienced an outbreak and is conducting a health check of their environment! What Protection Technology should the SEP team enable to prevent vulnerability attacks on software?
Which action does the Shared Insight Cache (SIC) server take when the whitelist reaches maximum capacity?
What is a valid Symantec Endpoint Protection (SEP) single site design?
What is a function of Symantec Insight?
Which step is unnecessary when an administrator creates an application rule set?
A user is unknowingly about to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client's system.
In which feature set order must the threat pass through to successfully infect the system?
Which task is unavailable for administrative accounts that authenticate using RSA SecurID Authentication?
Which two criteria can an administrator use to determine hosts in a host group? (Select two.)
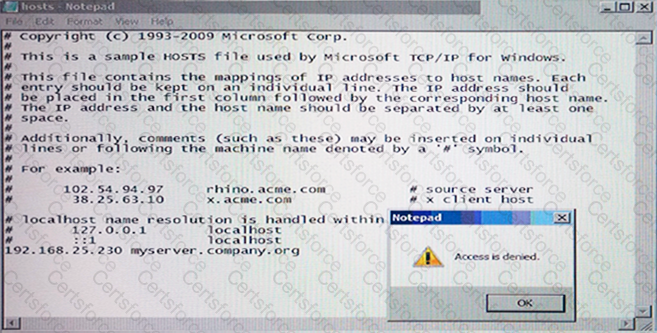
Why is Notepad unable to save the changes to the file in the image below?