Northern Trail Outfitters has had an increase in requests from other business units to integrate opportunity information with other systems from Salesforce. The developers have started writing asynchronous @future callouts directly into the target systems. The CIO is concerned about the viability of this approach and scaling for future growth. What should be done to mitigate the CIO’s concerns?
An enterprise customer with more than 10 million customers has a landscape including an Enterprise Billing System (EBS), a Document Management System (DMS), and Salesforce CRM. Customer Support needs seamless access to customer billing information from the EBS and generated bills from the DMS. Which authorization and authentication need should an integration consultant consider while integrating the DMS and EBS with Salesforce?
A new Salesforce program has the following high-level abstract requirement: Business processes executed on Salesforce require data updates between some internal systems and Salesforce. Which relevant details should a Salesforce integration architect seek to specifically solve for the integration architecture needs of the program?
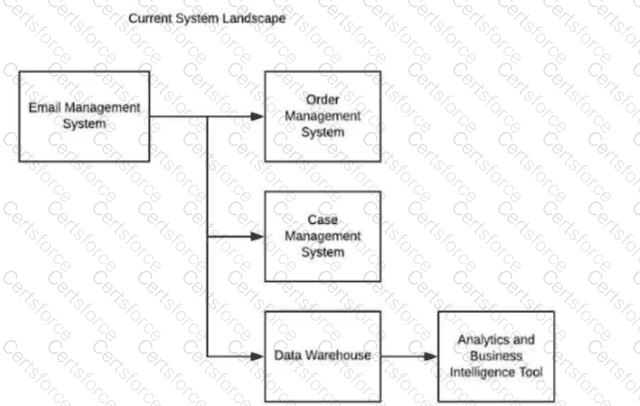
Considering Salesforce capabilities, what should the integration architect evaluate when integrating Salesforce with the current system landscape?
A media company recently implemented an IAM system supporting SAML and OpenId. The IAM system must integrate with Salesforce to give new self-service customers instant access to Salesforce Community Cloud. Which requirement should Salesforce Community Cloud support for self-registration and SSO?
The director of customer service at Northern Trail Outfitters (NTO) wants to capture and trend specific business events that occur in Salesforce in real time. The metrics will be accessed in an ad-hoc manner using an external analytics system. The events include product exchanges, authorization clicks, subscription cancellations, and refund initiations via Cases. Which solution should meet these business requirements?
An integration architect has designed a mobile application for Salesforce users to get data while on the road using a custom user interface (UI). The application is secured with OAuth and is currently functioning well. There is a new requirement where the mobile application needs to obtain the GPS coordinates and store them on a custom geolocation field. The geolocation field is secured with field-level security, so users can view the value without changing it. What should be don4e to meet the requirement?
An enterprise architect has requested the Salesforce integration architect to review the following (see diagram and description) and provide recommendations after carefully considering all constraints of the enterprise systems and Salesforce Platform limits.
About 3,000 phone sales agents use a Salesforce Lightning user interface (UI) concurrently to check eligibility of a customer for a qualifying offer.
There are multiple eligibility systems that provide this service and are hosted externally.
Their current response times could take up to 90 seconds to process and return.
These eligibility systems are accessed through APIs orchestrated via ESB (MuleSoft).
All requests from Salesforce traverse the customer's API Gateway layer, which imposes a timeout constraint of 9 seconds.
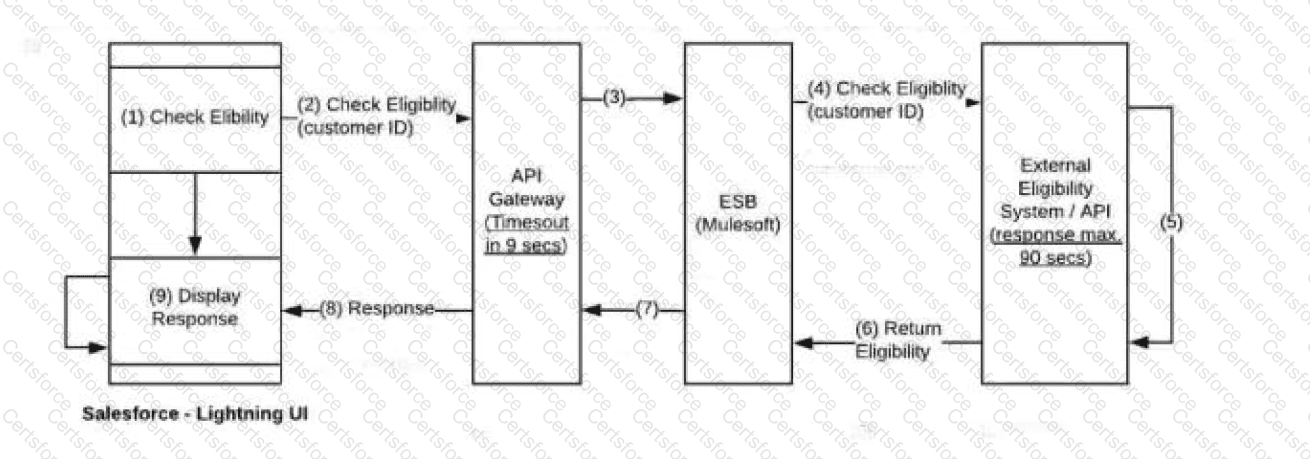
Which recommendation should the integration architect make?
Northern Trail Outfitters uses Salesforce to track leads and opportunities, and to capture order details. However, Salesforce isn’t the system that holds or processes orders. After the order details are captured in Salesforce, an order must be created in the Remote system, which manages the order’s lifecycle. The integration architect for the project is recommending a remote system that will subscribe to the platform event defined in Salesforce. Which integration pattern should be used for this business use case?
Northern Trail Outfitters (NTO) uses different shipping services for each of the 34 countries it serves. Services are added and removed frequently to optimize shipping times and costs. Sales representatives need to select between valid service(s) for the customer’s country and request shipping estimates from that service. Which solution should an architect propose?