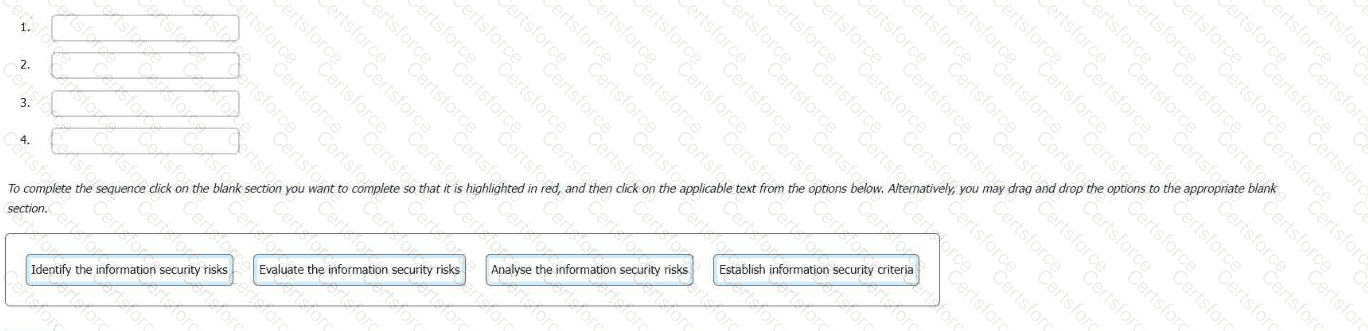
Select the correct sequence for the information security risk assessment process in an ISMS.
To complete the sequence click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the options to the appropriate blank
The auditor was unable to identify that Company A hid their insecure network architecture. What type of audit risk is this?
You are the audit team leader conducting a third-party audit of an online insurance organisation. During Stage 1, you found that the organisation took a very cautious risk approach and included all the information security controls in ISO/IEC 27001:2022 Appendix A in their Statement of Applicability.
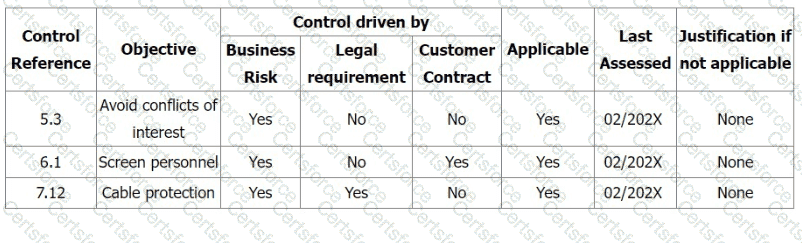
During the Stage 2 audit, your audit team found that there was no evidence of the implementation of the three controls (5.3 Segregation of duties, 6.1 Screening, 7.12 Cabling security) shown in the extract from the Statement of Applicability. No risk treatment plan was found.
Select three options for the actions you would expect the auditee to take in response to a
nonconformity against clause 6.1.3.e of ISO/IEC 27001:2022.
Scenario 2:
Clinic, founded in the 1990s, is a medical device company that specializes in treatments for heart-related conditions and complex surgical interventions. Based in Europe, it serves both patients and healthcare professionals. Clinic collects patient data to tailor treatments, monitor outcomes, and improve device functionality. To enhance data security and build trust, Clinic is implementing an information security management system (ISMS) based on ISO/IEC 27001. This initiative demonstrates Clinic's commitment to securely managing sensitive patient information and proprietary technologies.
Clinic established the scope of its ISMS by solely considering internal issues, interfaces, dependencies between internal and outsourced activities, and the expectations of interested parties. This scope was carefully documented and made accessible. In defining its ISMS, Clinic chose to focus specifically on key processes within critical departments such as Research and Development, Patient Data Management, and Customer Support.
Despite initial challenges, Clinic remained committed to its ISMS implementation, tailoring security controls to its unique needs. The project team excluded certain Annex A controls from ISO/IEC 27001 while incorporating additional sector-specific controls to enhance security. The team evaluated the applicability of these controls against internal and external factors, culminating in the development of a comprehensive Statement of Applicability (SoA) detailing the rationale behind control selection and implementation.
As preparations for certification progressed, Brian, appointed as the team leader, adopted a self-directed risk assessment methodology to identify and evaluate the company’s strategic issues and security practices. This proactive approach ensured that Clinic’s risk assessment aligned with its objectives and mission.
Question:
Does the Clinic's SoA document meet the ISO/IEC 27001 requirements for the SoA?
You are an experienced ISMS audit team leader providing guidance to an auditor in training.
The auditor in training appears to be confused about the interpretation of competence in ISO 27001:2022 and is seeking clarification from you that his understanding is correct. He sets out a series of mini scenarios and asks you which of these you would attribute to a lack of competence. Select four correct options.
What is we do in ACT - From PDCA cycle
Question
Which statement below best describes the relationship between information security elements?
Question
An organization requires all employees to undergo security awareness training every six months. The training covers topics such as recognizing phishing attacks, handling sensitive data, and reporting security incidents. After completing the training, employees must pass a short quiz to demonstrate their understanding.
What type of control does this activity represent?
Question
The auditor discovered that two out of 15 employees of the IT Department did not receive adequate information security training. What does this represent?
Scenario 1: Fintive is a distinguished security provider for online payments and protection solutions. Founded in 1999 by Thomas Fin in San Jose, California, Fintive
offers services to companies that operate online and want to improve their information security, prevent fraud, and protect user information such as PII. Fintive centers
its decision-making and operating process based on previous cases. They gather customer data, classify them depending on the case, and analyze them. The company
needed a large number of employees to be able to conduct such complex analyses. After some years, however, the technology that assists in conducting such analyses
advanced as well. Now, Fintive is planning on using a modern tool, a chatbot, to achieve pattern analyses toward preventing fraud in real-time. This tool would also be
used to assist in improving customer service.
This initial idea was communicated to the software development team, who supported it and were assigned to work on this project. They began integrating the chatbot
on their existing system. In addition, the team set an objective regarding the chatbot which was to answer 85% of all chat queries.
After the successful integration of the chatbot, the company immediately released it to their customers for use. The chatbot, however, appeared to have some issues.
Due to insufficient testing and lack of samples provided to the chatbot during the training phase, in which it was supposed "to learn" the queries pattern, the chatbot
failed to address user queries and provide the right answers. Furthermore, the chatbot sent random files to users when it received invalid inputs such as odd patterns
of dots and special characters. Therefore, the chatbot was unable to properly answer customer queries and the traditional customer support was overwhelmed with
chat queries and thus was unable to help customers with their requests.
Consequently, Fintive established a software development policy. This policy specified that whether the software is developed in-house or outsourced, it will undergo a
black box testing prior to its implementation on operational systems.
Based on this scenario, answer the following question:
The chatbot was supposed "to learn" the queries pattern to address user queries and provide the right answers. What type of technology enables
this?