Where are tags applied to control access to Generative AI when implementing AI Access Security?
A company has a Prisma Access deployment for mobile users in North America and Europe. Service connections are deployed to the data centers on these continents, and the data centers are connected by private links.
With default routing mode, which action will verify that traffic being delivered to mobile users traverses the service connection in the appropriate regions?
An engineer configures a Security policy for traffic originating at branch locations in the Remote Networks configuration scope. After committing the configuration and reviewing the logs, the branch traffic is not matching the Security policy.
Which statement explains the branch traffic behavior?
An engineer deploys a new branch connected to Prisma Access. From the customer premises equipment (CPE) device at the branch, Phase 1 on the tunnel is established, but Phase 2-encrypted packets are not coming back from Prisma Access.
Which Strata Logging Service log facility should the engineer review to determine why Phase 2-encrypted traffic is not being received?
How can an engineer verify that only the intended changes will be applied when modifying Prisma Access policy configuration in Strata Cloud Manager (SCM)?
A customer is implementing Prisma Access (Managed by Strata Cloud Manager) to connect mobile users, branch locations, and business-to- business (B2B) partners to their data centers.
The solution must meet these requirements:
The mobile users must have internet filtering, data center connectivity, and remote site connectivity to the branch locations.
The branch locations must have internet filtering and data center connectivity.
The B2B partner connections must only have access to specific data center internally developed applications running on non-standard ports.
The security team must have access to manage the mobile user and access to branch locations.
The network team must have access to manage only the partner access.
How should Prisma Access be implemented to meet the customer requirements?
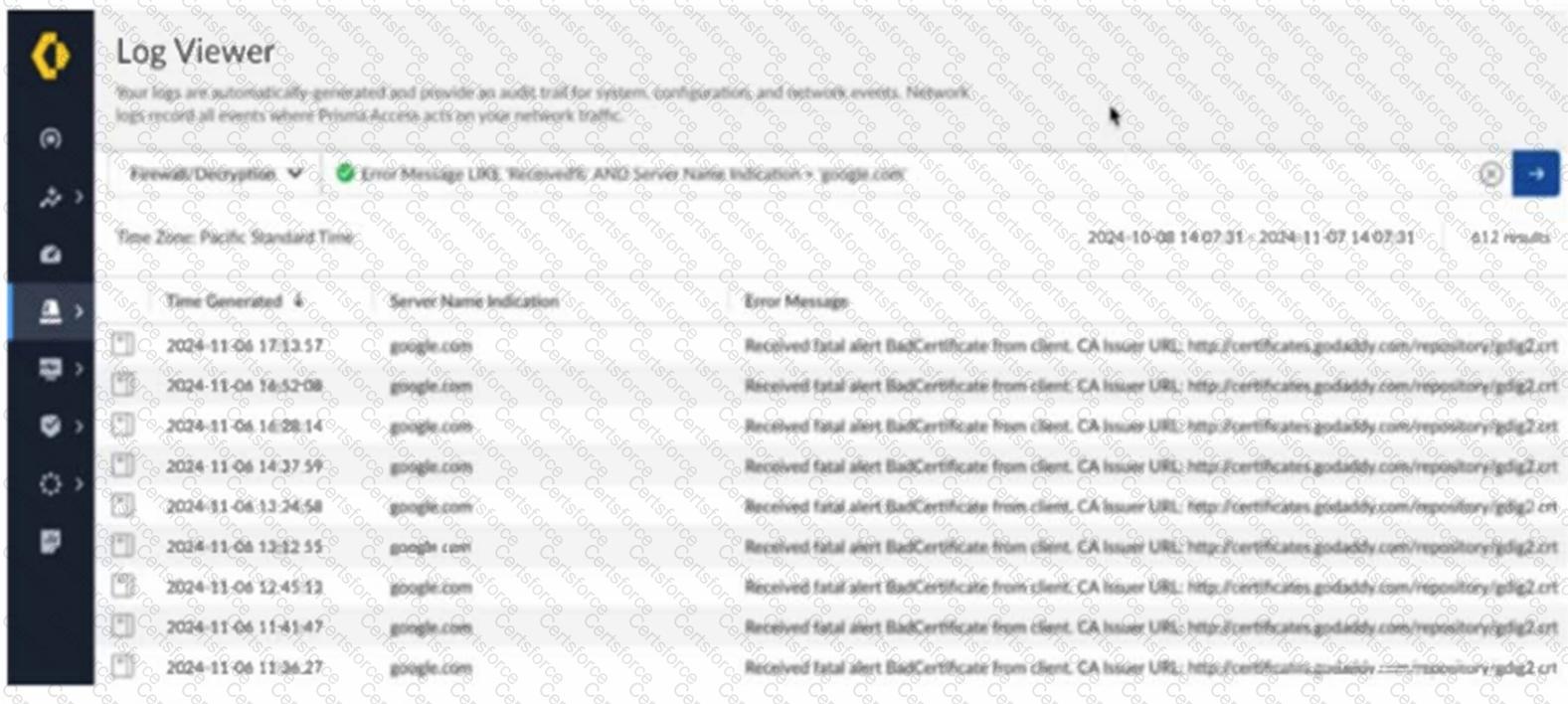
Based on the image below, which two statements describe the reason and action required to resolve the errors? (Choose two.)
An engineer has configured a Web Security rule that restricts access to certain web applications for a specific user group. During testing, the rule does not take effect as expected, and the users can still access blocked web applications.
What is a reason for this issue?
Which two statements apply when a customer has a large branch office with employees who all arrive and log in within a five-minute time period? (Choose two.)
How can a senior engineer use Strata Cloud Manager (SCM) to ensure that junior engineers are able to create compliant policies while preventing the creation of policies that may result in security gaps?