Console is running in a Kubernetes cluster, and Defenders need to be deployed on nodes within this cluster.
How should the Defenders in Kubernetes be deployed using the default Console service name?
Who can access saved searches in a cloud account?
Which action would be applicable after enabling anomalous compute provisioning?
Which report includes an executive summary and a list of policy violations, including a page with details for each policy?
A customer has a requirement to automatically protect all Lambda functions with runtime protection. What is the process to automatically protect all the Lambda functions?
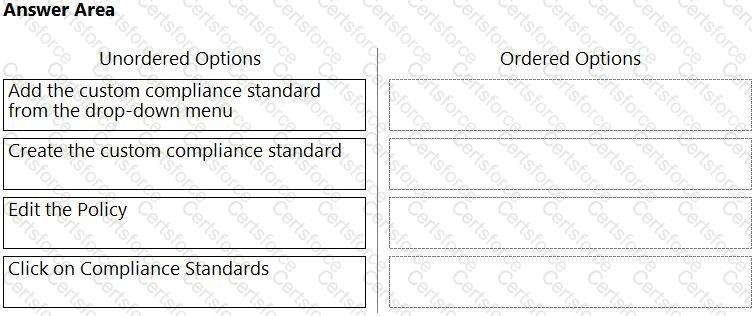
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)
Given the following RQL:
Which audit event snippet is identified by the RQL?
A)
B)
C)
D)
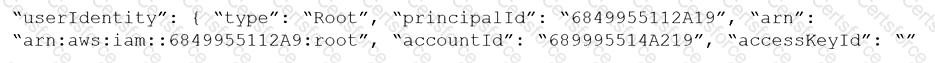
In which Console menu would an administrator verify whether a custom compliance check is failing or passing?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)