An administrator logs in to Prism Element goes to the Network view, and sees the output shown in the exhibit.
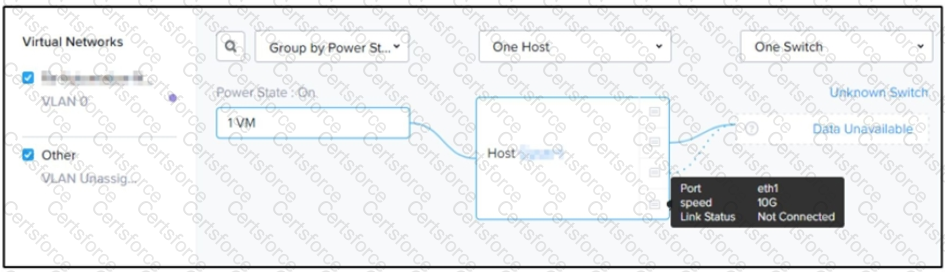
Which three steps must the administrator take to increase throughput to the host? (Choose three.)
When configuring Prism Central, which two log modules are able to forward messages to an external syslog server? (Choose two.)
Which algorithm do snapshots and clones leverage to maximize efficiency and effectiveness?
Which two access protocols are supported by Files? (Choose two.)
Where should an administrator unregister Prism Element from Prism Central?
An administrator is configuring data protection and DR for a multi-tier application. All VMs must be protected at the same time.
What must the administrator do to meet this requirement?
What are two minimum prerequisites for live migration to succeed? (Choose two.)
Which best practice should be followed when creating a bond in a Nutanix cluster?
Which two capabilities does IPAM provide in a Nutanix networking configuration? (Choose two.)
An administrator is working with Nutanix Support and needs to provide logs for troubleshooting an issue. The cluster is located in a secure environment. Data such as IP addresses and VM names cannot be shared.
Which method should be used to anonymize the log data sent to Nutanix Support?
A)

B)
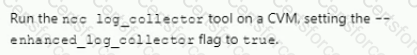
C)

D)
