You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to deploy a Microsoft Purview insider risk management solution that will generate an alert when users share sensitive information on Site1 with external recipients.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct answer is worth one point.
You implement Microsoft 36S Endpoint data loss pi event ion (Endpoint DIP).
You have computer that run Windows 11 and have Microsoft 365 Apps instated The computers are joined to a Microsoft Entra
tenant
You need to ensure that endpoint DIP policies can protect content on the computers.
Solution: You deploy the Microsoft Purview Information Protection client to the computers.
Does this meet the goal?
You have a Microsoft 365 E5 subscription. The subscription contains a user named User1 and the sensitivity labels shown in the following table.

You publish the labels to User1.
The subscription contains the files shown in the following table.
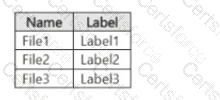
Which files can Microsoft 365 Copilot summarize for User1?
You have a Microsoft 365 E5 subscription that contains 500 Windows devices.
You plan to deploy Microsoft Purview Data Security Posture Management for AI (DSPM for AI).
You need to ensure that you can monitor user activities on third-party generative AI websites.
Which two prerequisites should you complete for DSPM for AI? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You are planning a data loss prevention (DLP) solution that will apply to Windows Client computers.
You need to ensure that when users attempt to copy a file that contains sensitive information to a USB storage device, the following requirements are met:
● If the users are members of a group named Group1, the users must be allowed to copy the file, and an event must be recorded in the audit log.
● All other users must be blocked from copying the file.
What should you create?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 tenant and 500 computers that run Windows 11. The computers are onboarded to Microsoft Purview.
You discover that a third-party application named Tailspin_scanner.exe accessed protected sensitive information on multiple computers. Tailspin_scanner.exe is installed locally on the computers.
You need to block Tailspin_scanner.exe from accessing sensitive documents without preventing the application from accessing other documents.
Solution: From the Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings, you add a folder path to the file path exclusions.
Does this meet the goal?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
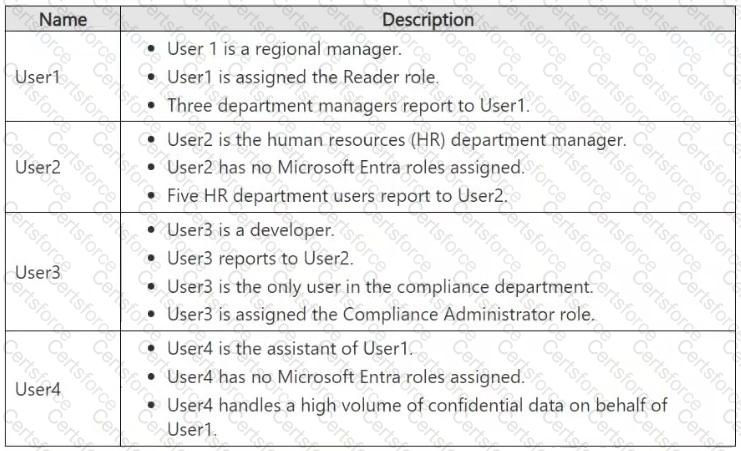
Which users will Microsoft Purview insider risk management flag as potential high-impact users?
You have 4 Microsoft 565 E5 subscription that contains two Microsoft SharePoint Online sites named Site1 and Site2. You plan to configure a retention label named Labe1 and apply label1 to all the files in Site1 You need to ensure that two years after a file is created in Site1. the file moves automatically to Site2. How should you configure the Choose what happens after the retention period setting for Label1?
You are creating a custom trainable classifier to Identify organizational product codes referenced in Microsoft 36S content. You identify 300 files to use as seed content When? should you store the seed content?
You have a Microsoft 365 E5 subscription that uses Microsoft Purview insider risk management and contains three users named User1, User2, and User3.
All insider risk management policies have adaptive protection enabled and the default conditions for insider risk levels configured.
The users perform the following activities, which trigger insider risk policy alerts:
User1 performs at least one data exfiltration activity that results in a high severity risk score.
User2 performs at least three risky user activities within seven days, that each results in a high severity risk score.
User3 performs at least bwo data exfiltration activities within seven days, that each results in a high severity risk score.
Which insider risk level is assigned to each user? To answer, drag the appropriate levels to the correct users. Each level may be used once, more than once, or not at all. You may need to drag the split bar between panes or seroll to view content.
NOTE: Each correct selection is worth one point.
