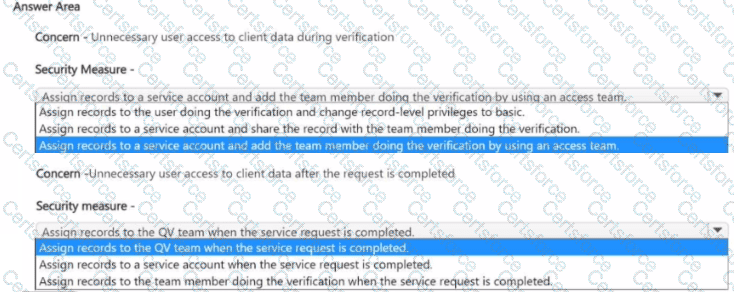
You need to address the unnecessary data access.
Which security changes should you make? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to implement the requirement for the VP of sales.
What should you do?
You need to set up the new service request completion process.
Which two components should you include in the solution? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You need to capture the Date Completed value from the website using a desktop flow.
Which method should you use?
You modify a model-driven app for a bicycle repair help desk. The model-driven app is for help desk users when customers have an issue with their bicycle.
After you add a custom table named bicycle, you configure the table for Microsoft Dataverse search. The table will contain information from callers about their bicycles. The account table is related to the custom table. Contact information is brought over to the custom table.
You add the following columns to the table:
Bicycle type
Tire brand
Special equipment
Users must be able to perform the following types of searches:
Search for all customers who have a bicycle type of Contoso and live in Florida.
Search all tables for any record that contains the word broken.
You need to decide which type of search will give you the results desired.
Which search should you configure? To answer, drag the appropriate search types to the correct requirements. Each search type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

A company uses Power Apps.
Users must be able to view only the address1 columns in the Account table.
You need to ensure other address columns are not visible to users when creating views and filters.
What should you do?
You deploy a Power Vitlu.il Agents chatoot that integrates with Dynamics 365 Omnichannel for Customer Service.
You observe that the chatbot is not able to recognize the questions asked by use's.
You need to ensure that the chatbot can respond to unrecognized questions. The solution must minimize administrative effort.
What should you do?
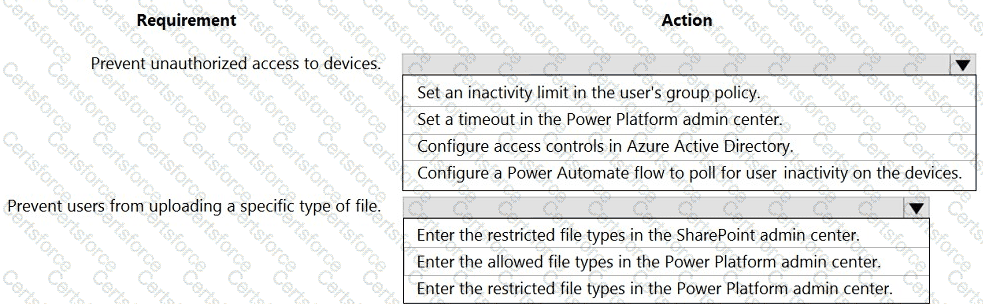
A company deploys several model-driven apps. The company uses shared devices in their warehouse. The devices are always powered on. Users log on to the devices and then launch the apps to perform actions.
Unauthorized users recently uploaded several files after another user failed to log out of a device. The company needs to prevent these incidents from occurring in the future.
You need to configure the solution to prevent the reported security incidents.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
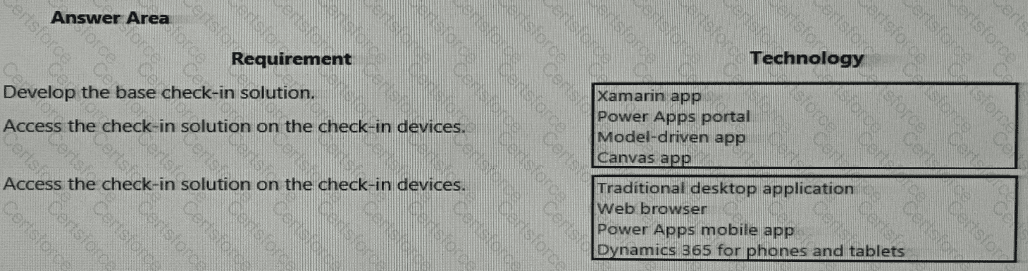
You need to design the guest check-in solution.
Which technologies should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to design the chat solution to answer the inquiry from Guest1.
Which three components can you use? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.