A DMZ web server has been compromised. During the log review, the incident responder wants to parse all common internal Class A addresses from the log. Which of the following commands should the responder use to accomplish this?
An intruder gains physical access to a company’s headquarters. The intruder is able to access the company’s network via a visitor’s office. The intruder sets up an attack device, under the visitor’s office desk, that impersonates the corporate wireless network. Users at headquarters begin to notice slow browsing speeds from their company laptops. Which of the following attacks is MOST likely occurring?
A high-level government official uses anonymous bank accounts to transfer a requested amount of funds to individuals in another country. These individuals are known for defacing government websites and exfiltrating sensitive data. Which of the following BEST describes the involved threat actors?
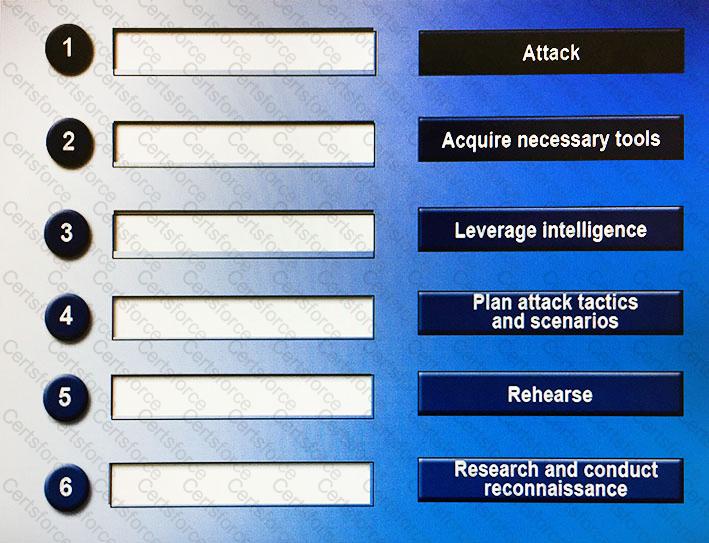
Drag and drop the following steps to perform a successful social engineering attack in the correct order, from first (1) to last (6).
A malicious attacker has compromised a database by implementing a Python-based script that will automatically establish an SSH connection daily between the hours of 2:00 am and 5:00 am. Which of the following is the MOST common motive for the attack vector that was used?
During review of a company’s web server logs, the following items are discovered:
2015-03-01 03:32:11 www.example.com/index.asp?id=-999 or 1=convert(int,@@version)—
2015-03-01 03:35:33 www.example.com/index.asp?id=-999 or 1=convert(int,db_name())—
2015-03-01 03:38:25 www.example.com/index.asp?id=-999 or 1=convert(int,user_name())—
Which of the following is depicted in the log example above?
An incident responder is asked to create a disk image of a compromised Linux server. Which of the following commands should be used to do this?
As part of an incident response effort, data has been collected and analyzed, and a malware infection has been contained. Which of the following is the NEXT step the incident response team should take within the incident response process?
When investigating a wireless attack, which of the following can be obtained from the DHCP server?
A user reports a pop-up error when starting a Windows machine. The error states that the machine has been infected with a virus and instructs the user to download a new antivirus client. In which of the following locations should the incidentresponder check to find what is generating the error message? (Choose two.)