According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
You are asked to look at a configuration that is designed to take all traffic with a specific source ip address and forward the
traffic to a traffic analysis server for further evaluation. The configuration is no longer working as intended.
Referring to the exhibit which change must be made to correct the configuration?
Exhibit
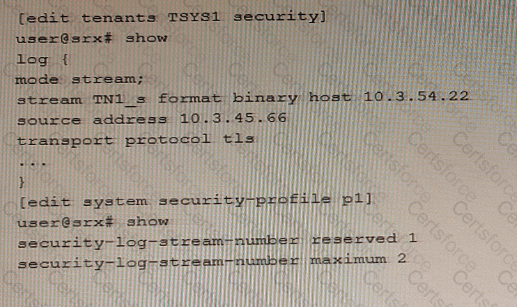
An administrator wants to configure an SRX Series device to log binary security events for tenant systems.
Referring to the exhibit, which statement would complete the configuration?
You want to enroll an SRX Series device with Juniper ATP Appliance. There is a firewall device in the path between the devices. In this scenario, which port should be opened in the firewall device?
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
You opened a support ticket with JTAC for your Juniper ATP appliance. JTAC asks you to set up access to the device
using the reverse SSH connection.Which three setting must be configured to satisfy this request? (Choose three.)
Exhibit
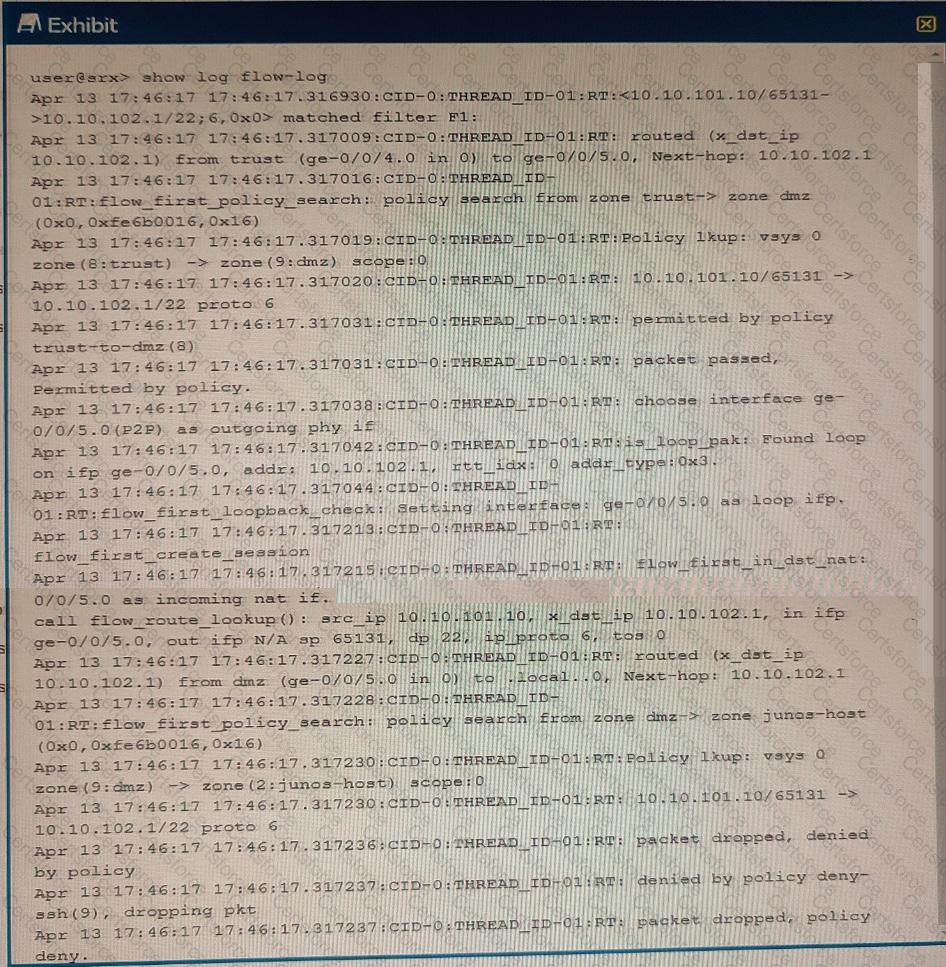
You are using traceoptions to verify NAT session information on your SRX Series device. Referring to the exhibit, which two statements are correct? (Choose two.)
You are asked to share threat intelligence from your environment with third party tools so that those
tools can be identify and block lateral threat propagation from compromised hosts.
Which two steps accomplish this goal? (Choose Two)
You want to enforce I DP policies on HTTP traffic.
In this scenario, which two actions must be performed on your SRX Series device? (Choose two )