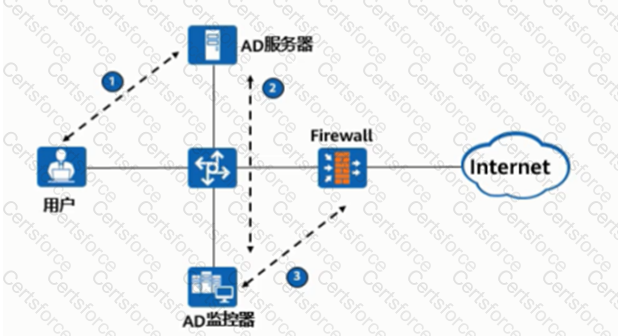
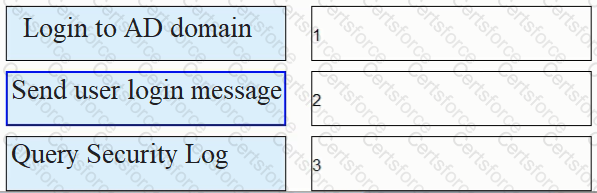
As shown in the figure, the process of AD single sign-on (querying the security log mode of AD server), please match the corresponding operation process.
Both digital envelopes and digital signatures guarantee data security and verify the origin of data.
When the Layer 2 switch receives a unicast frame and the MAC address table entry of the switch is empty, the switch discards the unicast frame.
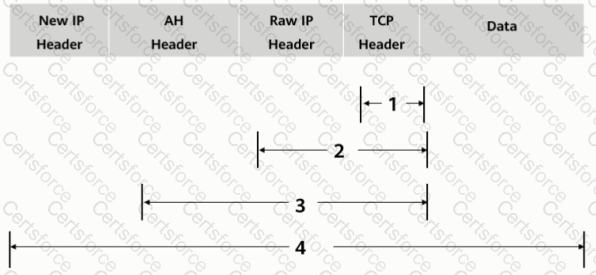
As shown in the figure, what is the authentication range of the AH protocol in tunnel mode?
WAF can accurately control and manage users' online behavior and user traffic.
The keys used by the IPSec encryption and authentication algorithms can be configured manually or dynamically negotiated via the ____ protocol. (abbreviation, all uppercase).
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*
Which of the following is the correct sequence for incident response management
1. Detection 2 Report 3 Mitigation 4 Lessons learned 5 Fix 6 Recovery 7 Response
What are the correct entries in the following description of firewall security zones?
The network environment is becoming more and more complex, and network security incidents occur frequently. While accelerating the construction of informatization, enterprises must not only resist external attacks, but also prevent internal management personnel from being involved in data leakage and operation and maintenance accidents due to operational errors and other issues. Which of the following options might reduce operational risk?