What is one way a noneypot can be used to launch a man-in-the-middle (MITM) attack to wireless clients?
Refer to the exhibit.
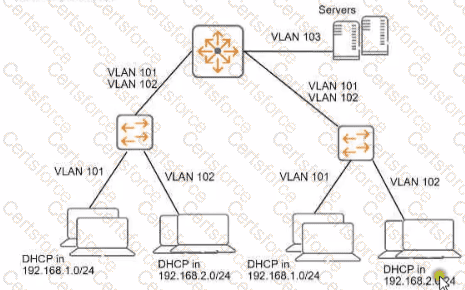
You need to ensure that only management stations in subnet 192.168.1.0/24 can access the ArubaOS-Switches' CLI. Web Ul. and REST interfaces The company also wants to let managers use these stations to access other parts of the network What should you do?
You have an Aruba solution with multiple Mobility Controllers (MCs) and campus APs. You want to deploy a WPA3-Enterprise WLAN and authenticate users to Aruba ClearPass Policy Manager (CPPM) with EAP-TLS.
What is a guideline for ensuring a successful deployment?
A company has a WLAN that uses Tunnel forwarding mode and WPA3-Enterprise security, supported by an Aruba Mobility Controller (MC) and campus APs (CAPs). You have been asked to capture packets from a wireless client connected to this WLAN and submit the packets to the security team.
What is a guideline for this capture?
You have been asked to send RADIUS debug messages from an ArubaOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command: logging 10.5.6.12
You enter this command: debug radius all
What is the correct debug destination?
You have been asked to rind logs related to port authentication on an ArubaOS-CX switch for events logged in the past several hours But. you are having trouble searching through the logs What is one approach that you can take to find the relevant logs?
What is a reason to set up a packet capture on an Aruba Mobility Controller (MC)?
A company has an ArubaOS solution. The company wants to prevent users assigned to the "user_group1" role from using gaming and peer-to-peer applications.
What is the recommended approach for these requirements?
What is an example of passive endpoint classification?
A client has accessed an HTTPS server at myhost1.example.com using Chrome. The server sends a certificate that includes these properties:
Subject name: myhost.example.com
SAN: DNS: myhost.example.com; DNS: myhost1.example.com
Extended Key Usage (EKU): Server authentication
Issuer: MyCA_SigningThe server also sends an intermediate CA certificate for MyCA_Signing, which is signed by MyCA. The client’s Trusted CA Certificate list does not include the MyCA or MyCA_Signing certificates.Which factor or factors prevent the client from trusting the certificate?