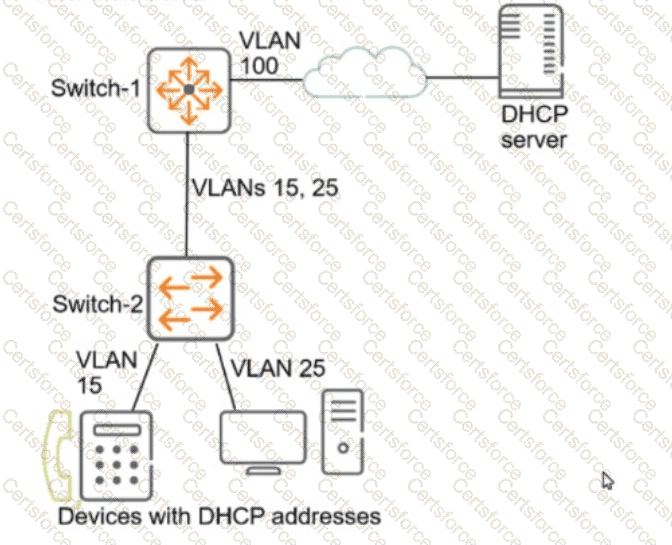
The scenario involves AOS-CX switches in a two-tier topology with Switch-1 as the core switch (default router) on VLAN 100 and Switch-2 as an access layer switch with VLANs 15 and 25, where end-user devices connect. The goal is to protect against exploits from untrusted end-user devices, such as DHCP spoofing or ARP poisoning attacks, which are common threats in access layer networks.
DHCP Snooping: This feature protects against rogue DHCP servers by filtering DHCP messages. It should be enabled on the access layer switch (Switch-2) where end-user devices connect, specifically on the VLANs where these devices reside (VLANs 15 and 25). DHCP snooping builds a binding table of legitimate IP-to-MAC mappings, which can be used by other features like ARP inspection.
ARP Inspection: This feature prevents ARP poisoning attacks by validating ARP packets against the DHCP snooping binding table. It should also be enabled on the access layer switch (Switch-2) on VLANs 15 and 25, where untrusted devices are connected.
Option B, "On Switch-2, enable DHCP snooping globally and on VLANs 15 and 25. Later, enable ARP inspection on the same VLANs," is correct. DHCP snooping must be enabled first to build the binding table, and then ARP inspection can use this table to validate ARP packets. This configuration should be applied on Switch-2, the access layer switch, because that’s where untrusted end-user devices connect.
Option A, "On Switch-1, enable ARP inspection on VLAN 100 and DHCP snooping on VLANs 15 and 25," is incorrect. Switch-1 is the core switch and does not directly connect to end-user devices on VLANs 15 and 25. DHCP snooping and ARP inspection should be enabled on the access layer switch (Switch-2) where the devices reside. Additionally, enabling ARP inspection on VLAN 100 (where the DHCP server is) is unnecessary since the DHCP server is a trusted device.
Option C, "On Switch-2, enable BPDU filtering on all edge ports in order to prevent eavesdropping attacks by untrusted devices," is incorrect. BPDU filtering is used to prevent spanning tree protocol (STP) attacks by blocking BPDUs on edge ports, but it does not protect against eavesdropping or other exploits like DHCP spoofing or ARP poisoning, which are more relevant in this context.
Option D, "On Switch-1, enable DHCP snooping on VLAN 100 and ARP inspection on VLANs 15 and 25," is incorrect for the same reason as Option A. Switch-1 is not the appropriate place to enable these features since it’s not directly connected to the untrusted devices on VLANs 15 and 25.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"DHCP snooping should be enabled on access layer switches where untrusted end-user devices connect. It must be enabled globally and on the specific VLANs where the devices reside (e.g., dhcp-snooping vlan 15,25). This feature builds a binding table of IP-to-MAC mappings, which can be used by Dynamic ARP Inspection (DAI) to prevent ARP poisoning attacks. DAI should also be enabled on the same VLANs (e.g., ip arp inspection vlan 15,25) after DHCP snooping is configured, ensuring that ARP packets are validated against the DHCP snooping binding table." (Page 145, DHCP Snooping and ARP Inspection Section)
Additionally, the guide notes:
"Dynamic ARP Inspection (DAI) and DHCP snooping are typically configured on access layer switches to protect against exploits from untrusted devices, such as DHCP spoofing and ARP poisoning. These features should be applied to the VLANs where end-user devices connect, not on core switches unless those VLANs are directly connected to untrusted devices." (Page 146, Best Practices Section)
[References:, HPE Aruba Networking AOS-CX 10.12 Security Guide, DHCP Snooping and ARP Inspection Section, Page 145., HPE Aruba Networking AOS-CX 10.12 Security Guide, Best Practices Section, Page 146.===========]