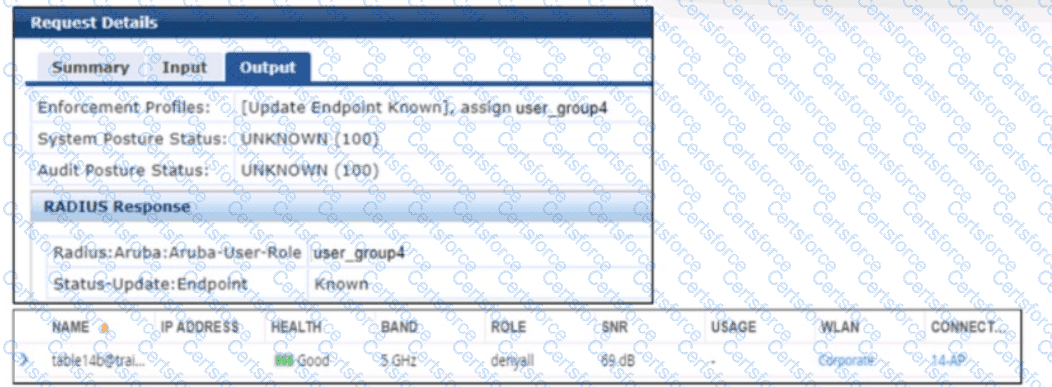
The scenario involves an AOS-8 Mobility Controller (MC) with a WLAN where a new user group has been added. Users in this group cannot connect to the WLAN, receiving errors indicating no Internet access and inability to reach resources. Exhibit 1 shows the ClearPass Policy Manager (CPPM) Access Tracker record for one user:
CPPM sends an Access-Accept with the VSA Radius:Aruba:Aruba-User-Role user_group4.
The endpoint is classified as "Known," but the user cannot access resources. Exhibit 2 (not provided but described) shows that the AOS device (MC) assigned the user’s client to the "denyall" role, which likely denies all access, explaining the lack of Internet and resource access.
Analysis:
CPPM sends the Aruba-User-Role VSA with the value "user_group4," indicating that the user should be assigned to the "user_group4" role on the MC.
However, the MC assigns the client to the "denyall" role, which typically denies all traffic, resulting in no Internet or resource access.
The issue lies in why the MC did not apply the "user_group4" role sent by CPPM.
Option A, "The AOS device does not have the correct RADIUS dictionaries installed on it to understand the Aruba-User-Role VSA," is incorrect. If the MC did not have the correct RADIUS dictionaries to understand the Aruba-User-Role VSA, it would not process the VSA at all, and the issue would likely affect all users, not just the new user group. Additionally, Aruba-User-Role is a standard VSA in AOS-8, and the dictionaries are built into the system.
Option B, "The AOS device has a server derivation rule configured on it that has overridden the role sent by CPPM," is incorrect. Server derivation rules on the MC can override roles sent by the RADIUS server (e.g., based on attributes like username or NAS-IP), but there is no indication in the scenario that such a rule is configured. If a derivation rule were overriding the role, it would likely affect more users, and the issue would not be specific to the new user group.
Option C, "The clients rejected the server authentication on their side because they do not have the root CA for CPPM’s RADIUS/EAP certificate," is incorrect. If the clients rejected the server authentication (e.g., due to a missing root CA for CPPM’s certificate), the authentication would fail entirely, and CPPM would not send an Access-Accept with the Aruba-User-Role VSA. The scenario confirms that authentication succeeded (Access-Accept was sent), so this is not the issue.
Option D, "The role name that CPPM is sending does not match the role name configured on the AOS device," is correct. CPPM sends the role "user_group4" in the Aruba-User-Role VSA, but the MC assigns the client to the "denyall" role. This suggests that the role "user_group4" does not exist on the MC, or there is a mismatch in the role name (e.g., due to case sensitivity, typos, or underscores vs. hyphens). In AOS-8, if the role specified in the Aruba-User-Role VSA does not exist on the MC, the MC falls back to a default role, which in this case appears to be "denyall," denying all access. The likely problem is that the role name "user_group4" sent by CPPM does not match the role name configured on the MC (e.g., it might be "user-group4" or a different name).
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When the Mobility Controller receives an Aruba-User-Role VSA in a RADIUS Access-Accept message, it attempts to assign the specified role to the client. If the role name sent by the RADIUS server (e.g., ‘user_group4’) does not match a role configured on the controller, the controller will fall back to a default role, such as ‘denyall,’ which may deny all access. To resolve this, ensure that the role name sent by the RADIUS server matches the role name configured on the controller, accounting for case sensitivity and naming conventions (e.g., underscores vs. hyphens)." (Page 306, Role Assignment Troubleshooting Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"A common issue when assigning roles via the Aruba-User-Role VSA is a mismatch between the role name sent by ClearPass and the role name configured on the Aruba device. If the role name does not match (e.g., ‘user_group4’ vs. ‘user-group4’), the device will not apply the intended role, and the client may be assigned a default role like ‘denyall,’ resulting in access issues. Verify that the role names match exactly in both ClearPass and the device configuration." (Page 290, RADIUS Role Assignment Issues Section)
[References:, HPE Aruba Networking AOS-8 8.11 User Guide, Role Assignment Troubleshooting Section, Page 306., HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide, RADIUS Role Assignment Issues Section, Page 290.===========]