Does this correctly describe the ArubaOS-CX architecture?
Solution: The ArubaOS-CX time-series database helps to support network analytics and troubleshooting.
AtubaOS-CX switches are acting as Virtual Extensible LAN (VXLAN) Tunnel Endpoints (VTEPs) WITHOUT Ethernet VPN (EVPN).
Does this correctly describe how the VTEPs handle VXLAN traffic forwarding?
Solution: VTEPs that use headend replication forward unicasts with unknown destination MAC addresses as unicast packets to each VTEP in the same VNl.
Is this a use case for disabling split-recovery mode on ArubaOS-CX switches in a Virtual Switching Extension (VSX) fabric?
Solution: You want to prevent any possibility of a split brain situation from occurring if the keepalive link fails some time after the ISL.
Two ArubaOS-CX switches ate part of a Virtual Switching Extension (V5X) fabric. Is this a guideline for configuring the switches' link-up delay settings?
Solution: Set the link-up delay timer based on the number of MAC forwarding, ARP, and routing table entries.
Is this a use case for disabling split-recovery mode on ArubaOS-CX switches in a Virtual Switching Extension (VSX) fabric?
Solution: You are not concerned about split brain Issues in your environment, so you want the secondary member to keep its links up if the ISL falls.
Does this correctly describe routing information advertised by a VXLAN Tunnel Endpoint (VTEP) that uses EVPN?
Solution: IMET routes advertise the MAC addresses that the VTEP has learned locally in a VXLAN.
Is this a difference between a typical data center network's requirements and a typical campus network's requirements?
Solution: Data center networks are typically less oversubscribed than campus networks.
Two ArubaOS-CX switches ate part of a Virtual Switching Extension (V5X) fabric. Is this a guideline for configuring the switches' link-up delay settings?
Solution: The link-up delay timer is only required when split-recovery is disabled.
Refer to the exhibit.
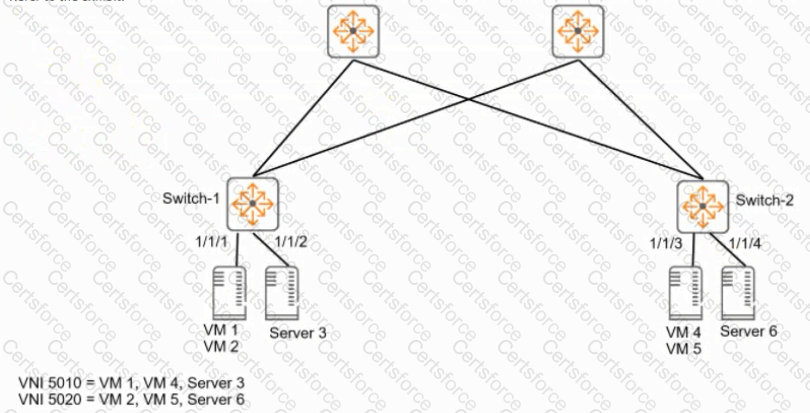
: The company wants AtubaOS-CX switches to provide VXLAN services for several VMs and servers, as shown in the exhibit. Hypervisors will not run VXLAN for this solution. Is this part of a valid configuration to meet the requirements?
Solution: Work with the server admins to assign a consistent VLAN for VMs 1 and 4. Assign interface 1/1/2 on Switch-1 to the same VLAN.
Refer to the exhibits.
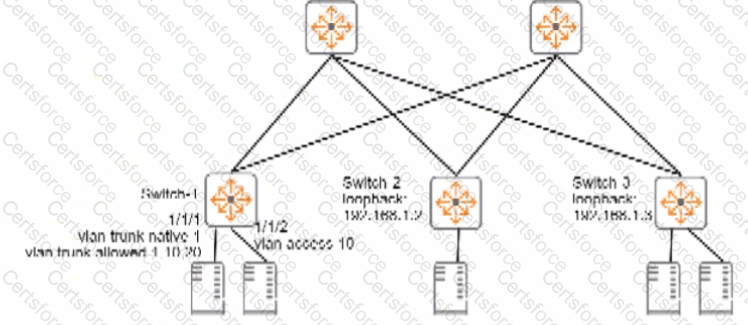
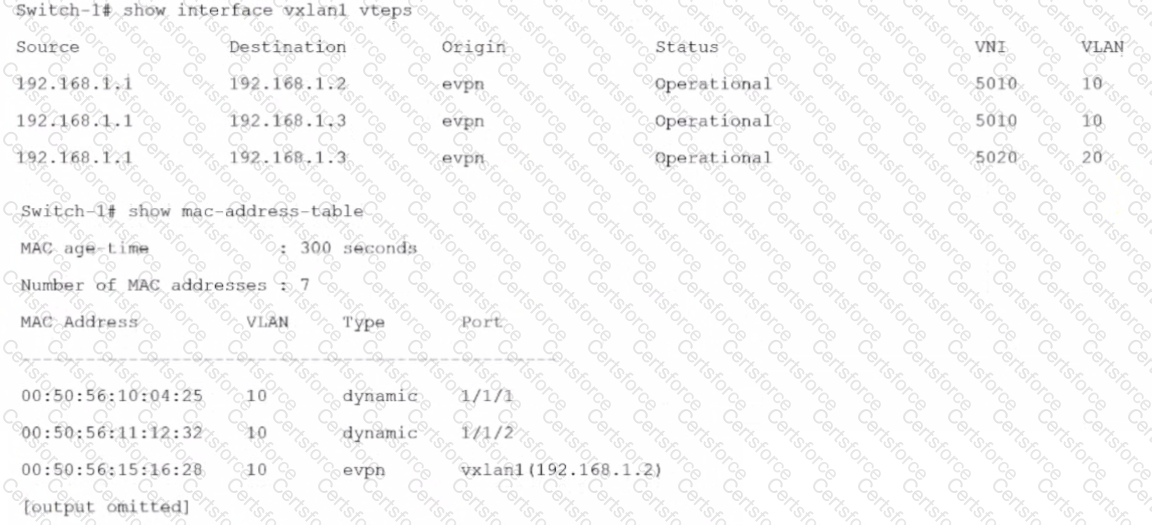
Is this how the switch handles the traffic?
Solution: A frame with destination MAC address, 00:50:56:00:00:03 arrives with a VLAN 10 tag on 1/1//1 on Switch-1. Switch-1 switches the frame out interface 1/1/2 without VXLAN.