You are the Security Administrator for an Internet Service Provider. From time to time your company gets subpoenas from attorneys and law enforcement for records of customers' access to the internet. What policies must you have in place to be prepared for such requests?
Choose the benefits of deploying switches over hubs in your infrastructure. (Choose two)
Which of the following recovery plans includes specific strategies and actions to deal with specific variances to assumptions resulting in a particular security problem, emergency, or state of affairs?
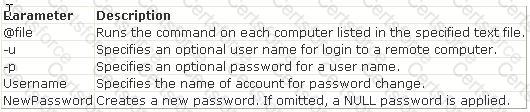
Adam works as a Security Analyst for Umbrella Inc. He is retrieving large amount of log data from syslog servers and network devices such as Router and switches. He is facing difficulty in analyzing the logs that he has retrieved. To solve this problem, Adam decides to use software called Sawmill. Which of the following statements are true about Sawmill?
In which of the following techniques does an attacker take network traffic coming towards a host at one port and forward it from that host to another host?
You work as a Network Administrator for XYZ CORP. The company has a TCP/IP-based network environment. The network contains Cisco switches and a Cisco router. A user is unable to access the Internet from Host B. You also verify that Host B is not able to connect to other resources on the network. The IP configuration of Host B is shown below:
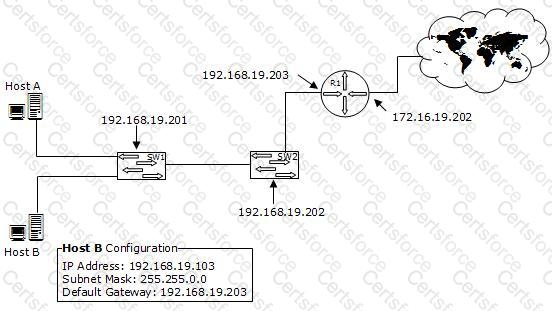
Which of the following is the most likely cause of the issue?
The following output is generated by running the show ip route command: RouterA#show ip route < - - Output Omitted for brevity - -> Which next hop address will RouterA use in forwarding traffic to 10.10.100.0/24?
Which of the following tools is used for port scanning?
Which of the following NFS mount options specifies whether a program using a file via an NFS connection should stop and wait for the server to come back online, if the host serving the exported file system is unavailable, or if it should report an error?
Mark works as a Network Administrator for Infonet Inc. The company has a Windows 2000 Active Directory domain-based network. The domain contains one hundred Windows XP Professional client computers. Mark is deploying an 802.11 wireless LAN on the network. The wireless LAN will use Wired Equivalent Privacy (WEP) for all the connections. According to the company's security policy, the client computers must be able to automatically connect to the wireless LAN. However, the unauthorized computers must not be allowed to connect to the wireless LAN and view the wireless network. Mark wants to configure all the wireless access points and client computers to act in accordance with the company's security policy. What will he do to accomplish this? (Choose three)