Which of the following commands can you use to search a string 'pwd' in all text files without opening them? (Choose two)
Which of the following commands can be used to find out where commands are located?
You work as a Network Administrator for XYZ CORP. The company's Windows 2000 network is configured with Internet Security and Acceleration (ISA) Server 2000. ISA Server is configured as follows: The server uses the default site and content rule and default IP packet filters. Packet filtering is enabled. The server has two protocol rules:
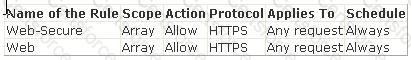
Users in the network complain that they are unable to access secure Web sites. However, they are able to connect to Web sites in which secure transmission is not required. What is the most likely cause?
John works as a Network Auditor for XYZ CORP. The company has a Windows-based network. John wants to conduct risk analysis for the company. Which of the following can be the purpose of this analysis? (Choose three)
What does a firewall check to prevent certain ports and applications from getting the packets into an Enterprise?
Which of the following policies helps reduce the potential damage from the actions of one person?
Which of the following key combinations in the vi editor is used to copy the current line?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He copies the whole structure of the We-are-secure Web site to the local disk and obtains all the files on the Web site. Which of the following techniques is he using to accomplish his task?
You work as a Network Administrator for ABC Inc. The company uses a secure wireless network. John complains to you that his computer is not working properly. What type of security audit do you need to conduct to resolve the problem?
Which of the following statements are true about locating rogue access points using WLAN discovery software such as NetStumbler, Kismet, or MacStumbler if you are using a Laptop integrated with Wi-Fi compliant MiniPCI card? (Choose two)