What is a limitation of deploying HIPS on a workstation?
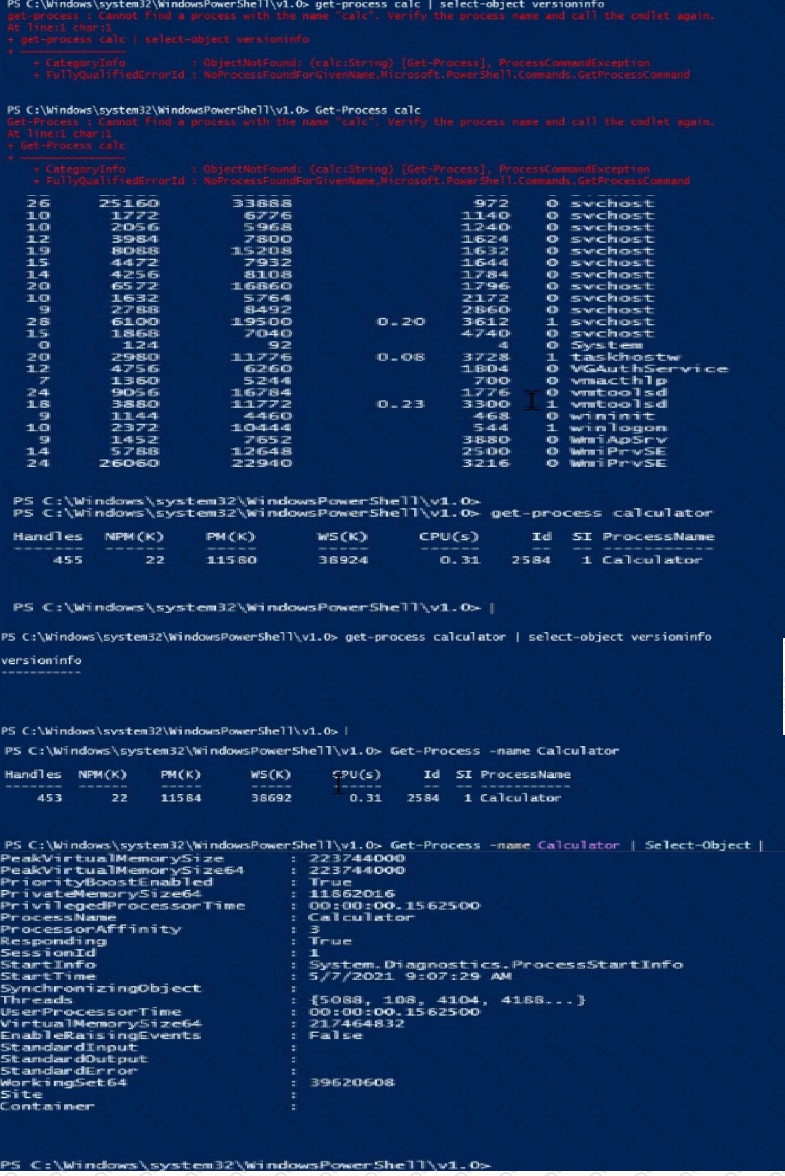
Launch Calculator (calc.exe). Using PowerShell, retrieve the Calculator Process Information. What is the value of the File Version property?
Hint: The process name of Calculator is calculator

Which Linux command could a systems administrator use to determine if an attacker had opened up a new listening port on her system?
Which of the following statements would describe the term "incident" when used in the branch of security known as Incident Handling?
Dilbert wants to have a script run on his Windows server every time Wally logs into it. Where should he place this script?
What is the function of the TTL (Time to Live) field in IPv4 and the Hop Limit field in IPv6 In an IP Packet header?
Use sudo to launch Snort with the, /etc /snort /snort.conf file In full mode to generate alerts based on incoming traffic to echo. What is the source IP address of the traffic triggering an alert with a destination port of 156?
Note: Snort Is configured to exit after It evaluates 50 packets.

When file integrity checking is enabled, what feature is used to determine if a monitored file has been modified?
Which of the following is an UDP based protocol?
If a DNS client wants to look up the IP address for good.news.com and does not receive an authoritative reply from its local DNS server, which name server is most likely to provide an authoritative reply?