Which of the following statements about policy is FALSE?
Which of the following commands is used to change file access permissions in Linux?
Your CIO has found out that it is possible for an attacker to clone your company's RFID (Radio Frequency ID) based key cards. The CIO has tasked you with finding a way to ensure that anyone entering the building is an employee. Which of the following authentication types would be the appropriate solution to this problem?
It is possible to sniff traffic from other hosts on a switched Ethernet network by impersonating which type of network device?
Which of the following is TRUE regarding Ethernet?
Which of the following is required to be backed up on a domain controller to recover Active Directory?
The Return on Investment (ROI) measurement used in Information Technology and Information Security fields is typically calculated with which formula?
Included below is the output from a resource kit utility run against local host.
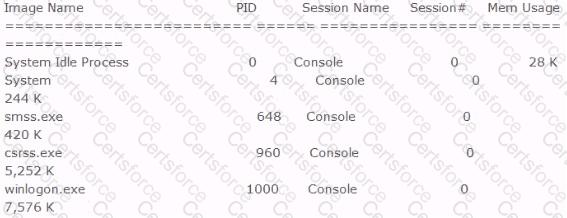
Which command could have produced this output?
Which of the following statements about IPSec are true?
Each correct answer represents a complete solution. Choose two.
What is achieved with the development of a communication flow baseline?