When trace route fails to get a timely response for a packet after three tries, which action will it take?
Which of the following is an advantage of an Intrusion Detection System?
What would the following IP tables command do?
IP tables -I INPUT -s 99.23.45.1/32 -j DROP
For most organizations, which of the following should be the highest priority when it comes to physical security concerns?
Which of the following access control principles helps prevent collusion and detect abuse of access?
Which of the following is a term that refers to unsolicited e-mails sent to a large number of e-mail users?
Which of the following ports is the default port for Layer 2 Tunneling Protocol (L2TP)?
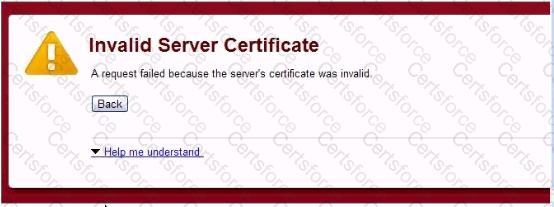
An employee attempting to use your wireless portal reports receiving the error shown below. Which scenario is occurring?
Which of the following are used to suppress gasoline and oil fires? Each correct answer represents a complete solution. Choose three.
A folder D:\Files\Marketing has the following NTFS permissions:
• Administrators: Full Control
• Marketing: Change and Authenticated
• Users: Read
It has been shared on the server as "MARKETING", with the following share permissions:
• Full Control share permissions for the Marketing group
Which of the following effective permissions apply if a user from the Sales group accesses the \\FILESERVER\MARKETING shared folder?