At which port does a DHCPv6 client listen for DHCP messages?
Maria works as a professional Ethical Hacker. She is assigned a project to test the security of www.we-are-secure.com. She wants to test a DoS attack on the We-are-secure server. She finds that the firewall of the server is blocking the ICMP messages, but it is not checking the UDP packets. Therefore, she sends a large amount of UDP echo request traffic to the IP broadcast addresses. These UDP requests have a spoofed source address of the We-are-secure server.
Which of the following DoS attacks is Maria using to accomplish her task?
Which of the following partitions contains the system files that are used to start the operating system?
You work as a Network Administrator for McNeil Inc. The company's Windows 2000-based network is configured with Internet Security and Acceleration (ISA) Server 2000. You configure intrusion detection on the server. Which of the following alerts notifies that repeated attempts to a destination computer are being made and no corresponding ACK (acknowledge) packet is being communicated?
Which of the following IP packet elements is responsible for authentication while using IPSec?
What netsh command should be run to enable IPv6 routing?
Each correct answer represents a part of the solution. Choose two.
Which of the following ICMPv6 neighbor discovery messages is sent by hosts to request an immediate router advertisement, instead of waiting for the next scheduled advertisement?
Which of the following is a correct sequence of different layers of Open System Interconnection (OSI) model?
Andrew, a bachelor student of Faulkner University, creates a gmail account. He uses 'Faulkner' as the password for the gmail account. After a few days, he starts receiving a lot of e-mails stating that his gmail account has been hacked. He also finds that some of his important mails have been deleted by someone. Which of the following methods has the attacker used to crack Andrew's password?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following applications cannot proactively detect anomalies related to a computer?
Peter works as a Technical Representative in a CSIRT for SecureEnet Inc. His team is called to investigate the computer of an employee, who is suspected for classified data theft. Suspect's computer runs on Windows operating system. Peter wants to collect data and evidences for further analysis. He knows that in Windows operating system, the data is searched in pre-defined steps for proper and efficient analysis. Which of the following is the correct order for searching data on a Windows based system?
Fill in the blank with the appropriate term.
___________is the practice of monitoring and potentially restricting the flow of information outbound from one network to another
Which of the following two cryptography methods are used by NTFS Encrypting File System (EFS) to encrypt the data stored on a disk on a file-by-file basis?
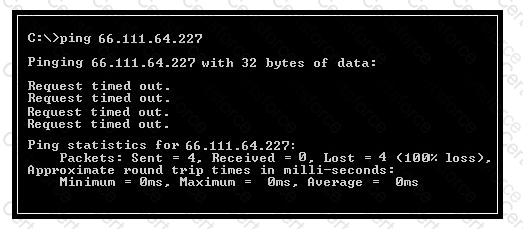
Which of the following conclusions can be drawn from viewing the given output generated by the PING command-line utility?
Which of the following is known as a message digest?