You work as a professional Computer Hacking Forensic Investigator. A project has been assigned to you to investigate Plagiarism occurred in the source code files of C#. Which of the following tools will you use to detect the software plagiarism?
An attacker wants to launch an attack on a wired Ethernet. He wants to accomplish the following tasks:
Sniff data frames on a local area network.
Modify the network traffic.
Stop the network traffic frequently.
Which of the following techniques will the attacker use to accomplish the task?
Victor wants to send an encrypted message to his friend. He is using certain steganography technique to accomplish this task. He takes a cover object and changes it accordingly to hide information. This secret information is recovered only when the algorithm compares the changed cover with the original cover. Which of the following Steganography methods is Victor using to accomplish the task?
Distributed Checksum Clearinghouse (DCC) is a hash sharing method of spam email detection.
Which of the following protocols does the DCC use?
You are the Administrator for a corporate network. You are concerned about denial of service attacks.
Which of the following would be the most help against Denial of Service (DOS) attacks?
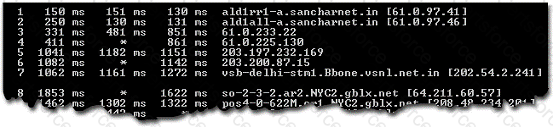
Which of the following utilities provides information as per the format given below?
You are planning DNS configuration for your company. You decide to configure an Active Directory integrated DNS.
Which of the following are the benefits of Active Directory integrated DNS configuration?
Each correct answer represents a complete solution. Choose all that apply.
You are implementing a host based intrusion detection system on your web server. You feel that the best way to monitor the web server is to find your baseline of activity (connections, traffic, etc.) and to monitor for conditions above that baseline. This type of IDS is called __________.
Which of the following types of attacks uses ICMP to consume bandwidth and crash sites?
What is the name of the group of blocks which contains information used by the operating system in Linux system?
Which of the following attacks is used to hack simple alphabetical passwords?
Which of the following ports can be used for IP spoofing?
Which of the following attacks is designed to deduce the brand and/or version of an operating system or application?
Which of the following are the two sub-layers present in Data Link layer of the OSI Reference model?
What is the maximum size of an IP datagram for Ethernet?