Adam, a malicious hacker purposely sends fragmented ICMP packets to a remote target. The total size of this ICMP packet once reconstructed is over 65,536 bytes.
On the basis of above information, which of the following types of attack is Adam attempting to perform?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. You want to know the current TCP/IP network configuration settings, DHCP server IP address, and DHCP lease expiration date of your network.
Which of the following utilities will you use?
Which of the following OSI layers is responsible for protocol conversion, data encryption/decryption, and data compression?
Which of the following is the default port for TACACS?
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
You work as a network administrator for BlueWell Inc. You have to convert your 48-bit host address (MAC address) to an IPv6 54-bit address. Using the IEEE-EUI-64 conversion process, how do you convert the 48-bit host address (MAC address) to an IPv6 54-bit address?
Which of the following is used to detect the bad sectors in a hard disk under Linux environment?
Which of the following statements best describes the string matching method of signature analysis?
Which of the following utilities can generate a local static route table?
Each correct answer represents a complete solution. Choose two.
Rick works as the Network Administrator of Baby Blue Inc. He wants to upgrade the existing network to the Active Directory based Windows 2000 network.
He configures a DNS on the network. Which of the following is the primary reason that the DNS is required in an Active Directory environment?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:
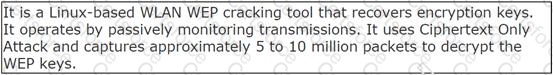
Which of the following tools is John using to crack the wireless encryption keys?
Which of the following IPv6 transition technologies is used by the DirectAccess if a user is in a remote location and a public IPv4 address, instead of public IPv6 address, has been assigned to the computer?
The National Shoes Inc. has an SNMP enabled router installed on its network. IT Manager wants to monitor all SNMP traffic generated by the router. So, he installs a Network Monitor on a Windows2000 Server computer on the network. The router is configured to send traps to an SNMP manager installed on another server. He wants to get a notification whenever the network router raises an SNMP trap. What will he do to achieve this?
(Click the Exhibit button on the toolbar to see the case study.)
Each correct answer represents a part of the solution. Choose two.
Adam works on a Linux system. He is using Sendmail as the primary application to transmit e-mails.
Linux uses Syslog to maintain logs of what has occurred on the system. Which of the following log files contains e-mail information such as source and destination IP addresses, date and time stamps etc?