Refer to The exhibit showing a FortiEDR configuration.
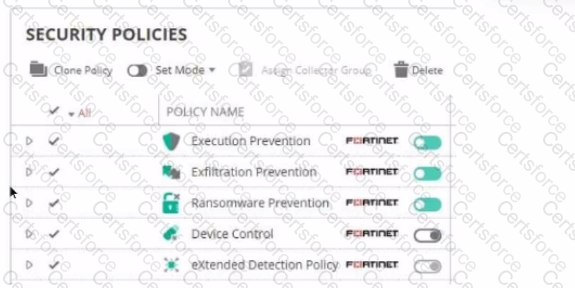
Based on the exhibit, which statement is correct?
An administrator has configured a FortiGate device to authenticate SSL VPN users using digital certificates. A FortiAuthenticator is the certificate authority (CA) and the Online Certificate Status Protocol (OCSP) server.
Part of the FortiGate configuration is shown below:
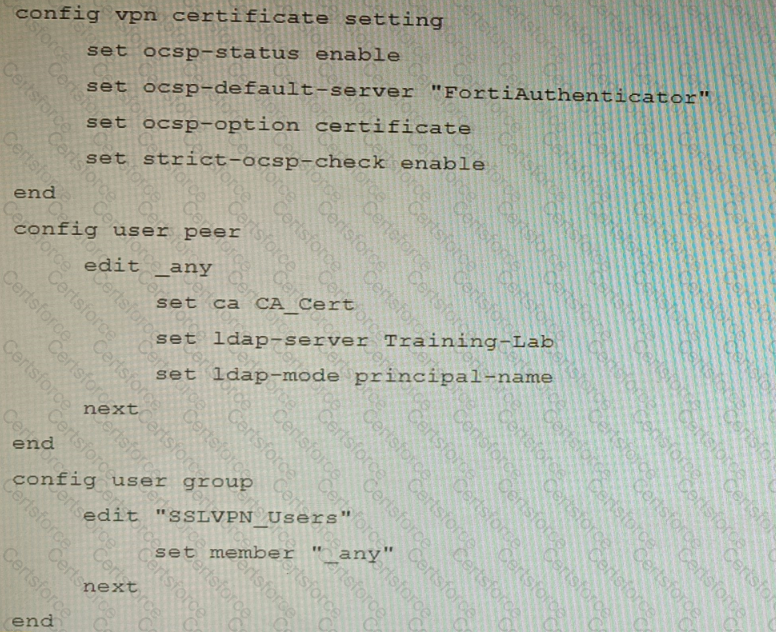
Based on this configuration, which two statements are true? (Choose two.)
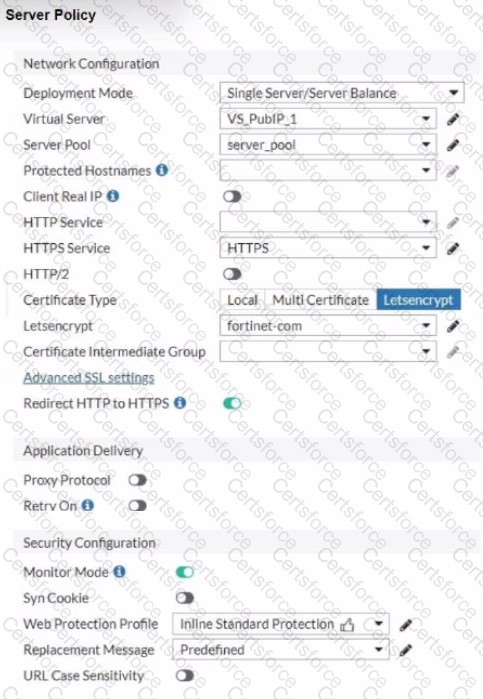
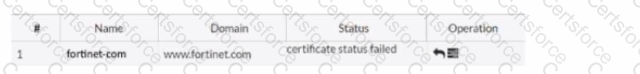
Refer to the exhibits.
You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.
Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)
Refer to the exhibit.
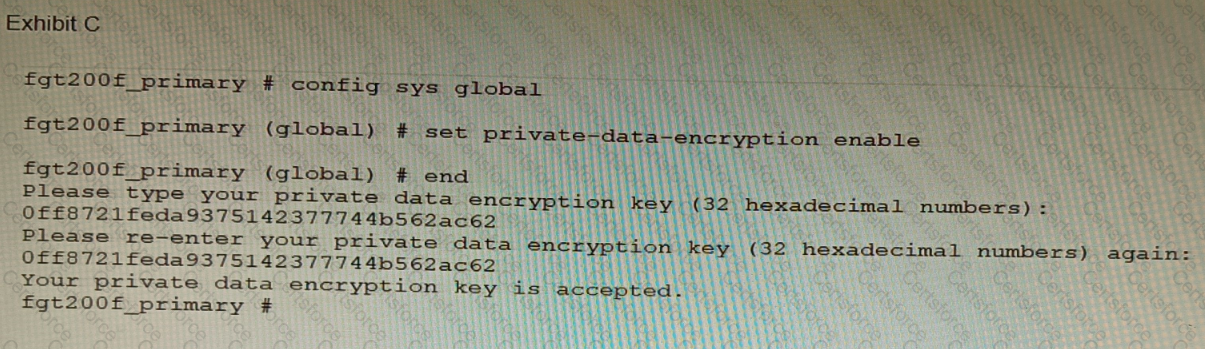
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains & TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
Refer to the exhibit showing a firewall policy configuration.
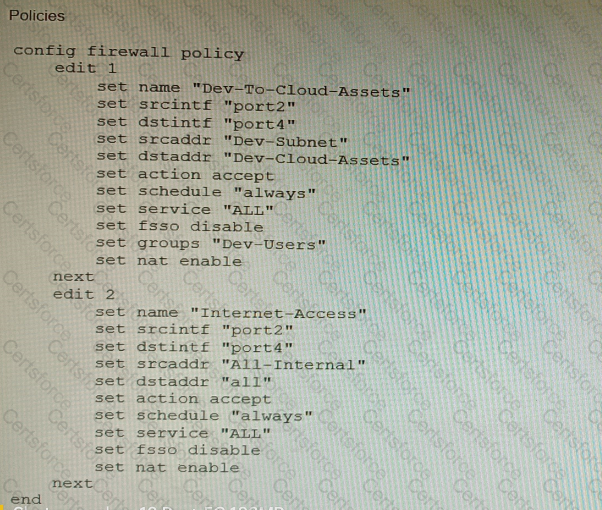
To prevent unauthorized access of their cloud assets, an administrator wants to enforce authentication on firewall policy ID 1.
What change does the administrator need to make?

Refer to the exhibit.
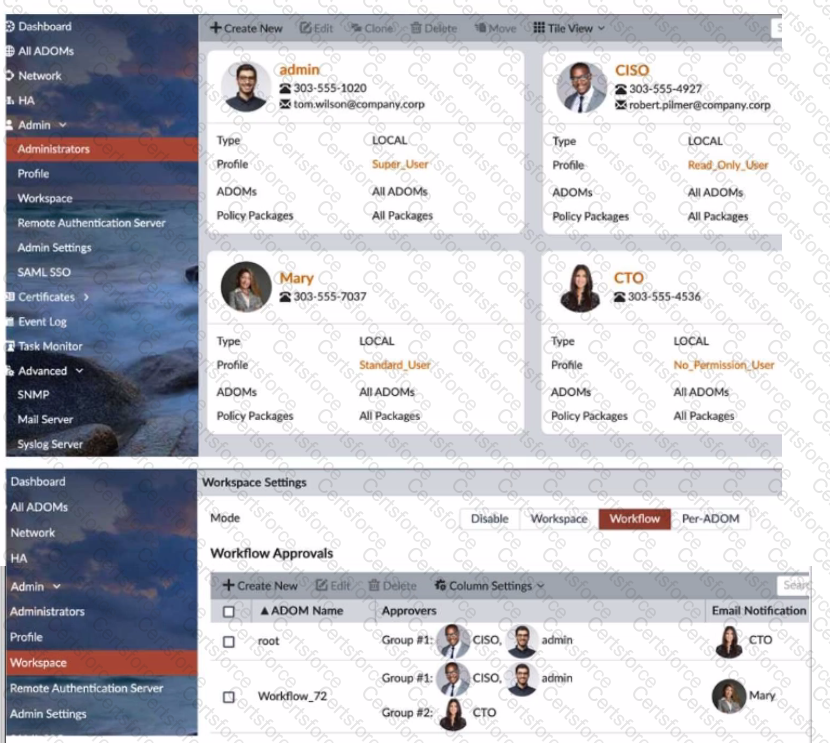
The Company Corp administrator has enabled Workflow mode in FortiManager and has assigned approval roles to the current administrators. However, workflow approval does not function as expected. The CTO is currently unable to approve submitted changes.
Given the exhibit, which two possible solutions will resolve the workflow approval problems with the Workflow_72 ADOM? (Choose two.)
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP.
What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
Refer to the exhibit.
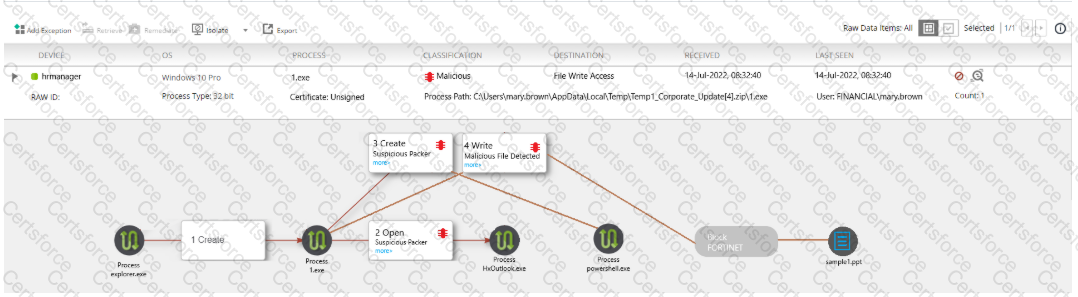
The exhibit shows the forensics analysis of an event detected by the FortiEDR core
In this scenario, which statement is correct regarding the threat?
Refer to the exhibit containing the configuration snippets from the FortiGate. Customer requirements:
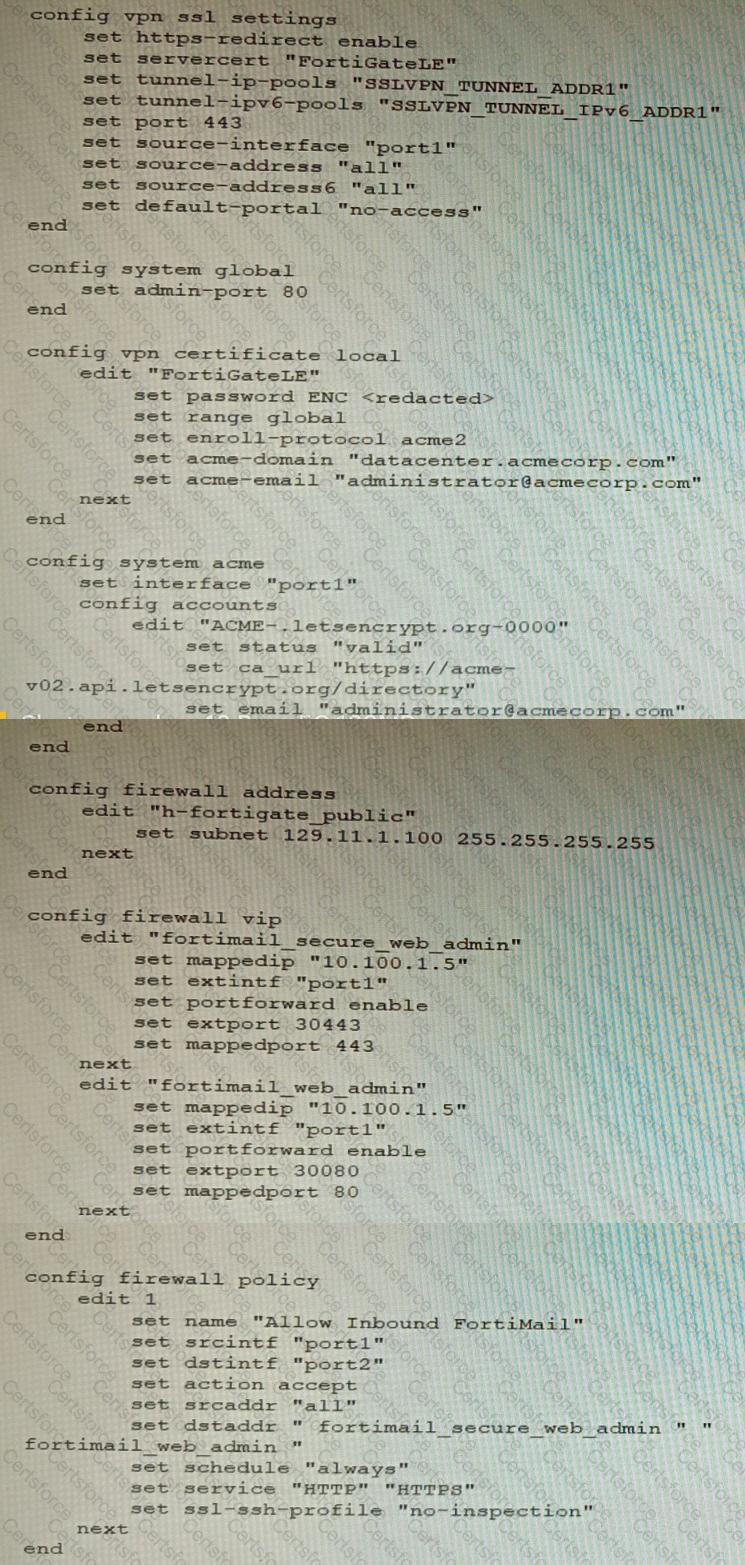
• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let's Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
A)
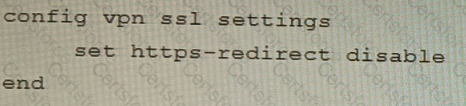
B)
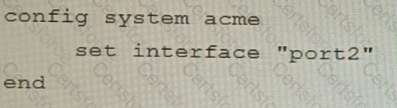
C)
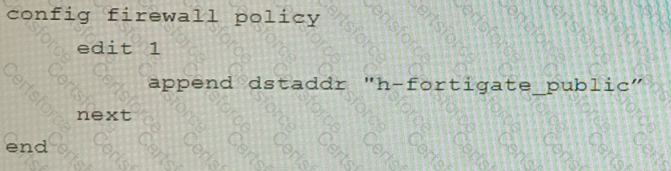
D)

Refer to the exhibits, which show a network topology and VPN configuration.
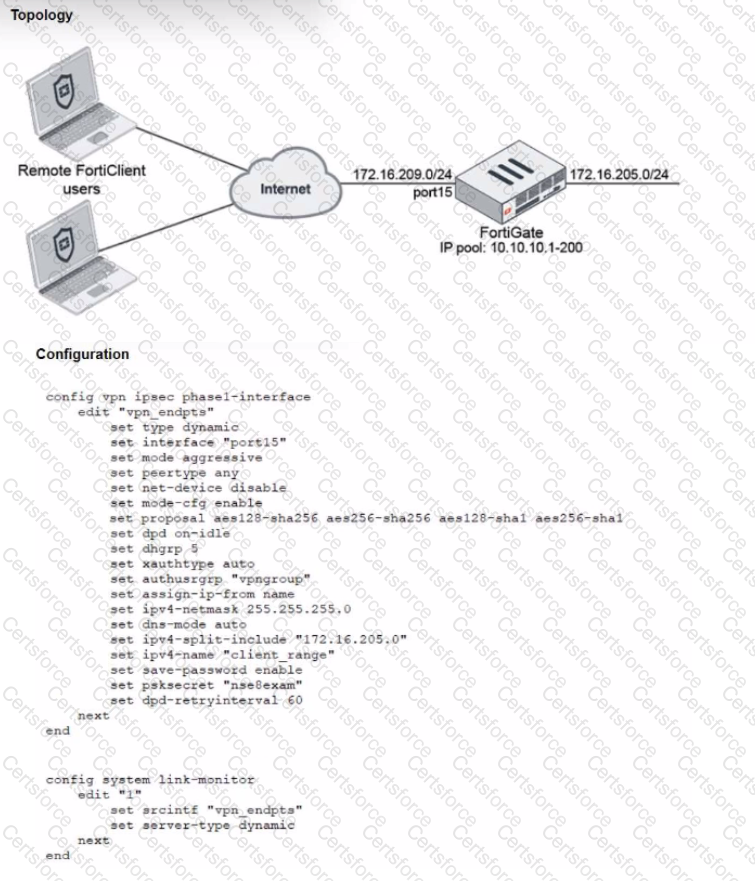
A network administrator has been tasked with modifying the existing dial-up IPsec VPN infrastructure to detect the path quality to the remote endpoints.
After applying the configuration shown in the configuration exhibit, the VPN clients can still connect and access the protected 172.16.205.0/24 network, but no SLA information shows up for the client tunnels when issuing the diagnose sys link-monitor tunnel all command on the FortiGate CLI.
What is wrong with the configuration?