Refer to the exhibit.
You notice that the custom event handler you configured to detect SMTP reconnaissance activities is creating a large number of events. This is overwhelming your notification system.
How can you fix this?
Which two best practices should be followed when exporting playbooks in FortiAnalyzer? (Choose two answers)
When does FortiAnalyzer generate an event?
Refer to the exhibits.
You configured a spearphishing event handler and the associated rule. However. FortiAnalyzer did not generate an event.
When you check the FortiAnalyzer log viewer, you confirm that FortiSandbox forwarded the appropriate logs, as shown in the raw log exhibit.
What configuration must you change on FortiAnalyzer in order for FortiAnalyzer to generate an event?
Refer to Exhibit:
A SOC analyst is creating the Malicious File Detected playbook to run when FortiAnalyzer generates a malicious file event. The playbook must also update the incident with the malicious file event data.
What must the next task in this playbook be?
Refer to the exhibits.
What can you conclude from analyzing the data using the threat hunting module?
Refer to the exhibits.
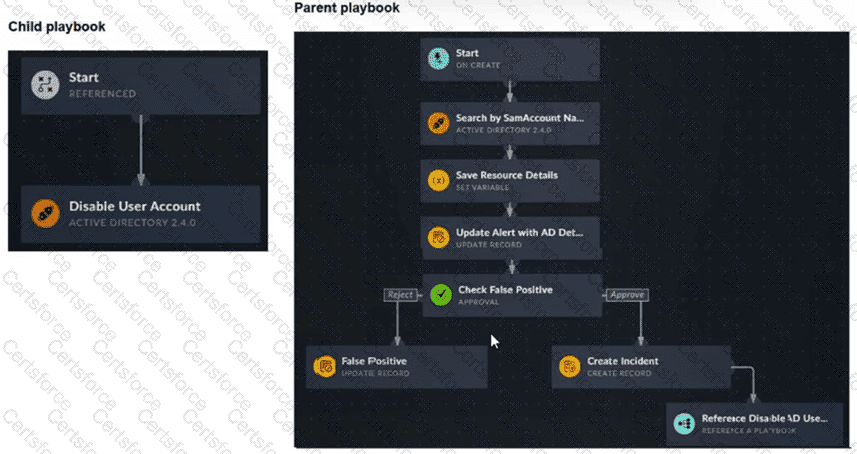
You have a playbook that, depending on whether an analyst deems the alert to be a true positive, could reference a child playbook. You need to pass variables from the parent playbook to the child playbook.
Place the steps needed to accomplish this in the correct order.
Which three statements accurately describe step utilities in a playbook step? (Choose three answers)
Refer to Exhibit:
You are tasked with reviewing a new FortiAnalyzer deployment in a network with multiple registered logging devices. There is only one FortiAnalyzer in the topology.
Which potential problem do you observe?
Which two playbook triggers enable the use of trigger events in later tasks as trigger variables? (Choose two.)