Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)
Refer to the exhibits.
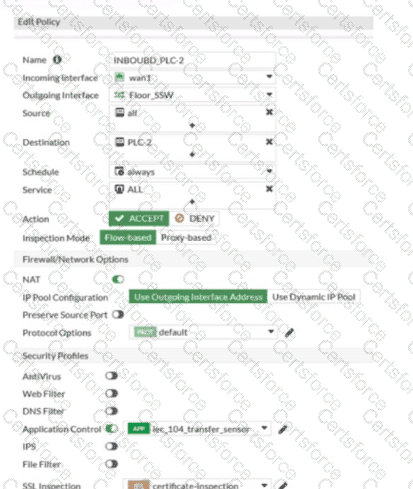
Which statement is true about the traffic passing through to PLC-2?
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
Refer to the exhibit.
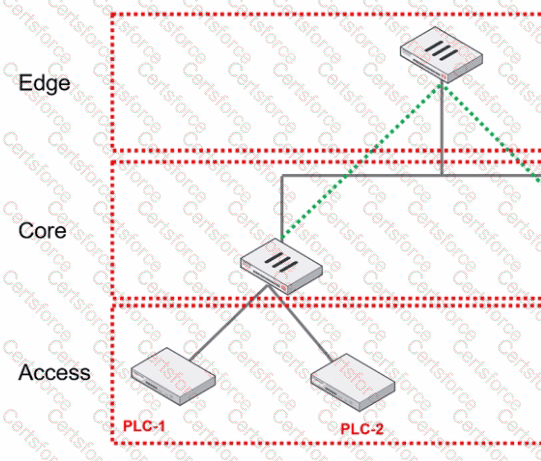
You are assigned to implement a remote authentication server in the OT network.
Which part of the hierarchy should the authentication server be part of?
Refer to the exhibit.
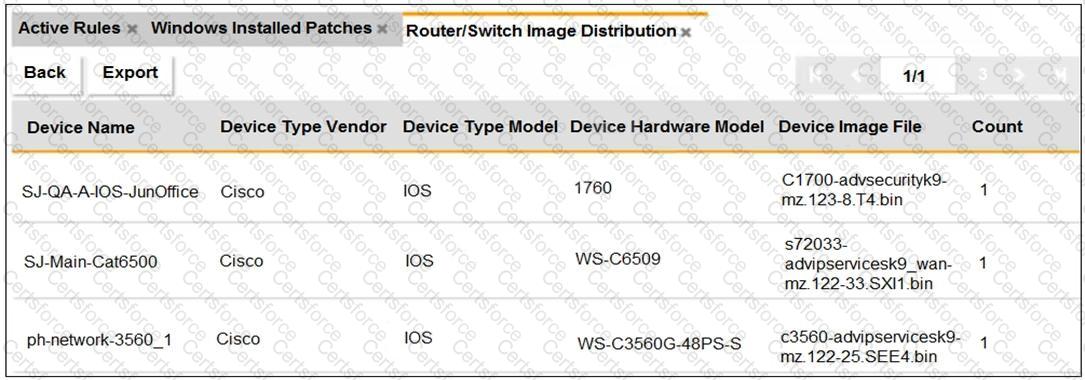
An OT administrator ran a report to identify device inventory in an OT network.
Based on the report results, which report was run?
Refer to the exhibit.
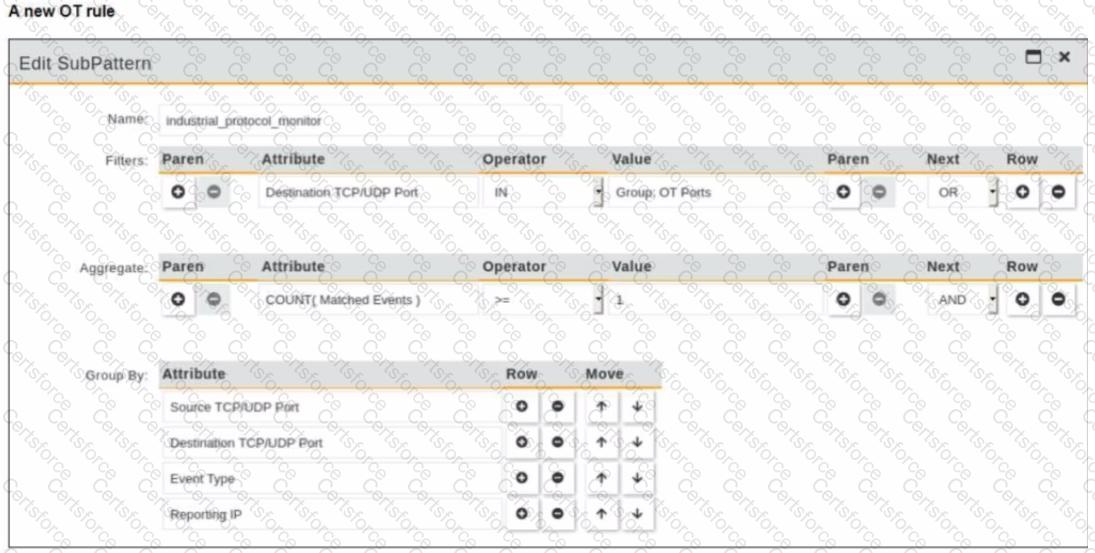
You are creating a new operational technology (OT) rule to monitor Modbus protocol traffic on FortiSIEM
Which action must you take to ensure that all Modbus messages on the network match the rule?
An OT supervisor needs to protect their network by implementing security with an industrial signature database on the FortiGate device.
Which statement about the industrial signature database on FortiGate is true?
As an OT network administrator you are managing three FortiGate devices that each protect different levels on the Purdue model To increase traffic visibility you are required to implement additional security measures to detect protocols from PLCs
Which security sensor must you implement to detect protocols on the OT network?
Which three Fortinet products can you use for device identification in an OT industrial control system (ICS)? (Choose three.)
Refer to the exhibit.
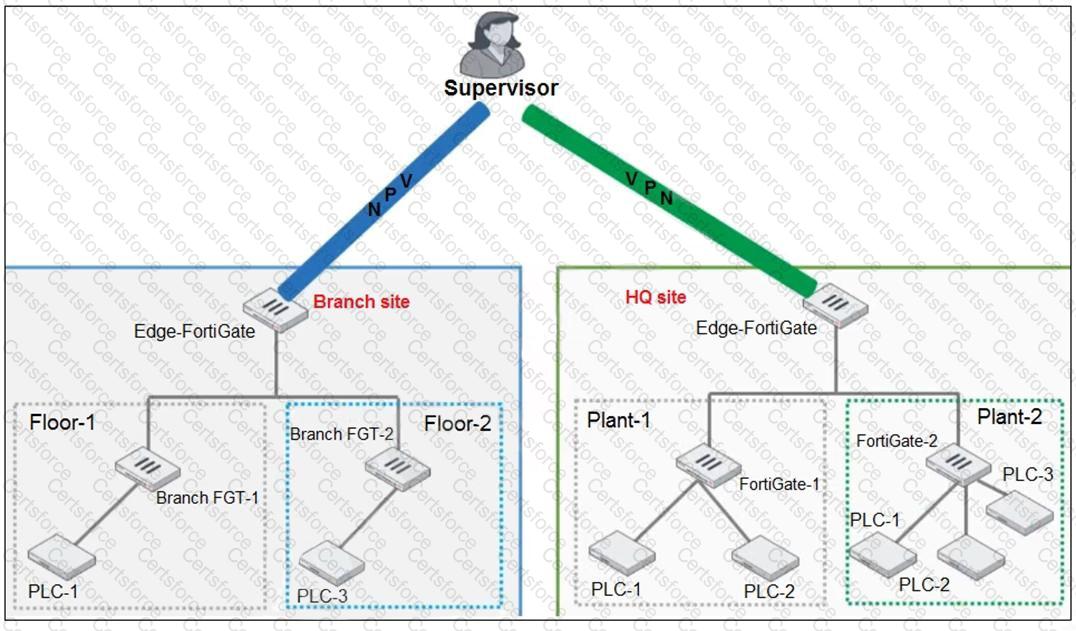
You need to configure VPN user access for supervisors at the breach and HQ sites using the same soft FortiToken. Each site has a FortiGate VPN gateway.
What must you do to achieve this objective?