Refer to the exhibit.
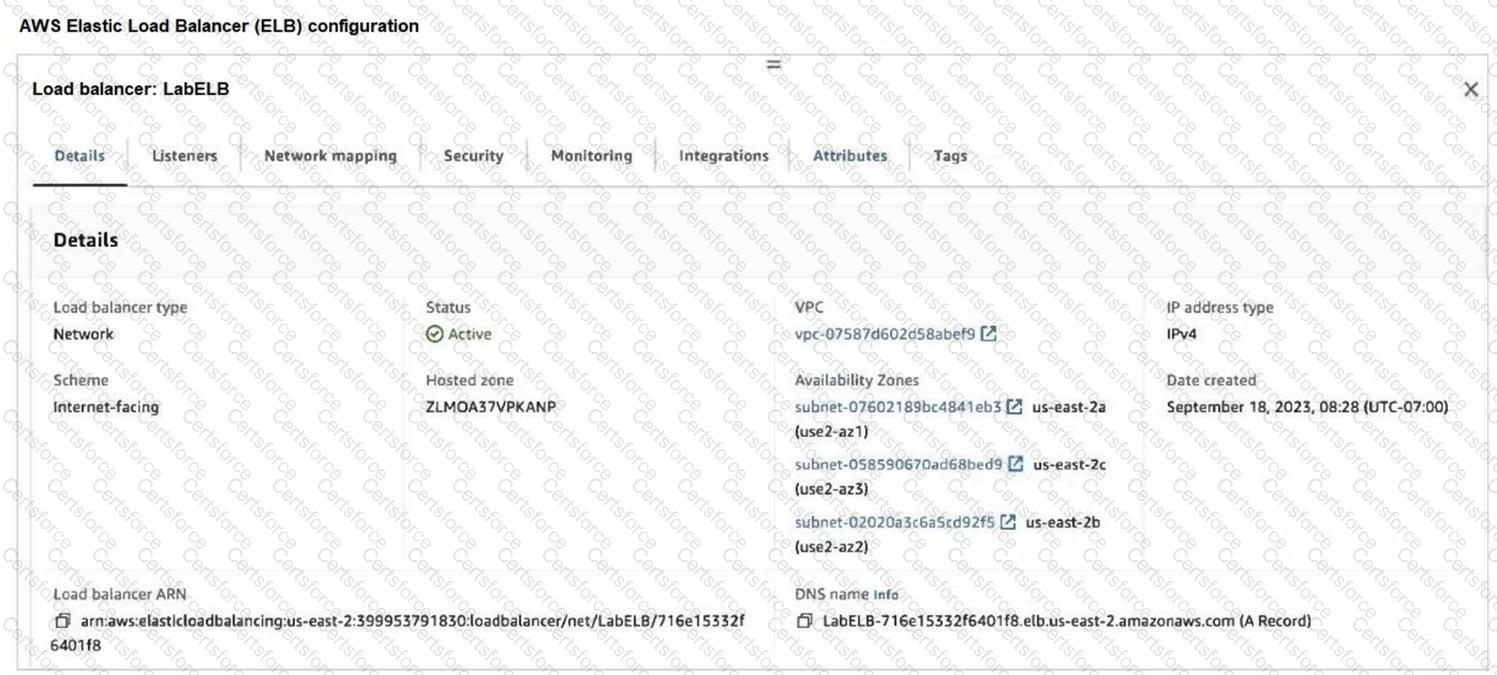
A customer is using the AWS Elastic Load Balancer (ELB).
Which two statements are correct about the ELB configuration? (Choose two.)
A customer has deployed FortiGate Cloud-Native Firewall (CNF).
Which two statements are correct about policy sets? (Choose two.)
You are troubleshooting network connectivity issues between two VMs deployed in AWS.
One VM is a FortiGate located on subnet "LAN" that is part of the VPC "Encryption". The other VM is a Windows server located on the subnet "servers" which is also in the "Encryption" VPC. You are unable to ping the Windows server from FortiGate.
What are two reasons for this? (Choose two.)
Refer to the exhibit.
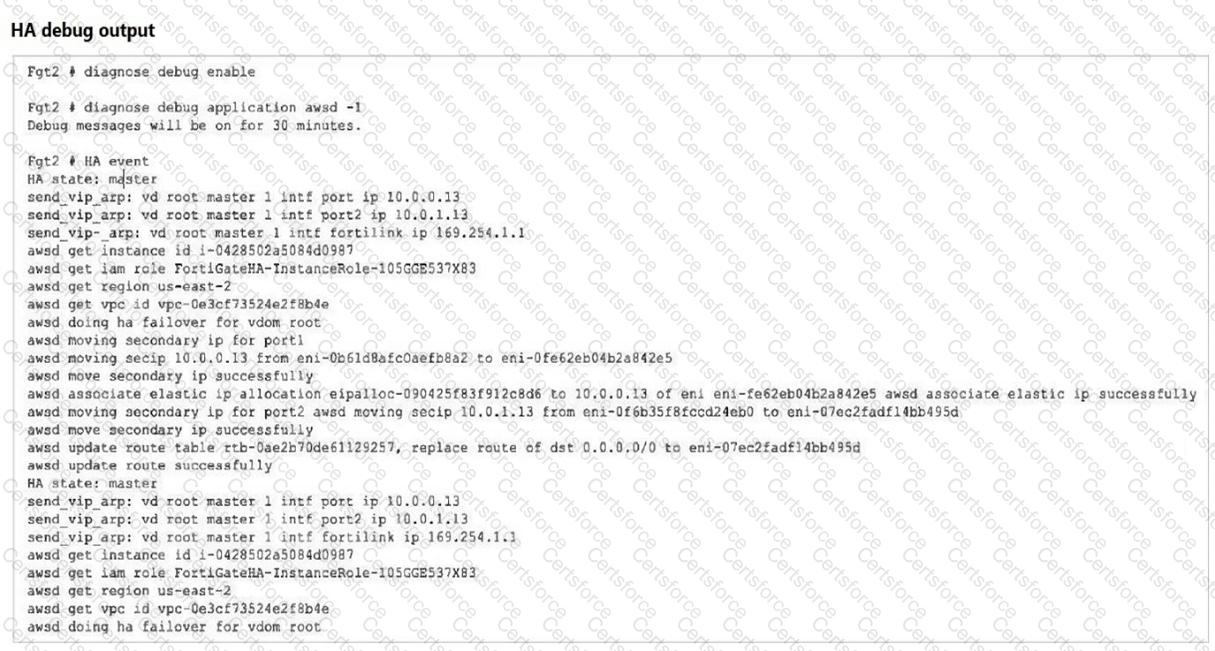
You deployed an active-passive FortiGate HA cluster using a CloudFormation template on an existing VPC. Now you want to test active-passive FortiGate HA failover by running a debug so you can see the API calls to change the Elastic and secondary IP addresses.
Which statement is correct about the output of the debug?
A customer has implemented GWLB between the partner and application VPCs. FortiGate appliances are deployed in the partner VPC with multiple AZs to inspect traffic transparently.
Which two things will happen to application traffic based on the GWLB deployment? (Choose two.)
AWS native network services offer vast functionality and inter-connectivity between the cloud and on-premises networks.
Which three additional functions can FortiGate for AWS offer to complement the native services offered by AWS? (Choose three.)
Which three statements are correct about VPC flow logs? (Choose three.)
Refer to the exhibit.
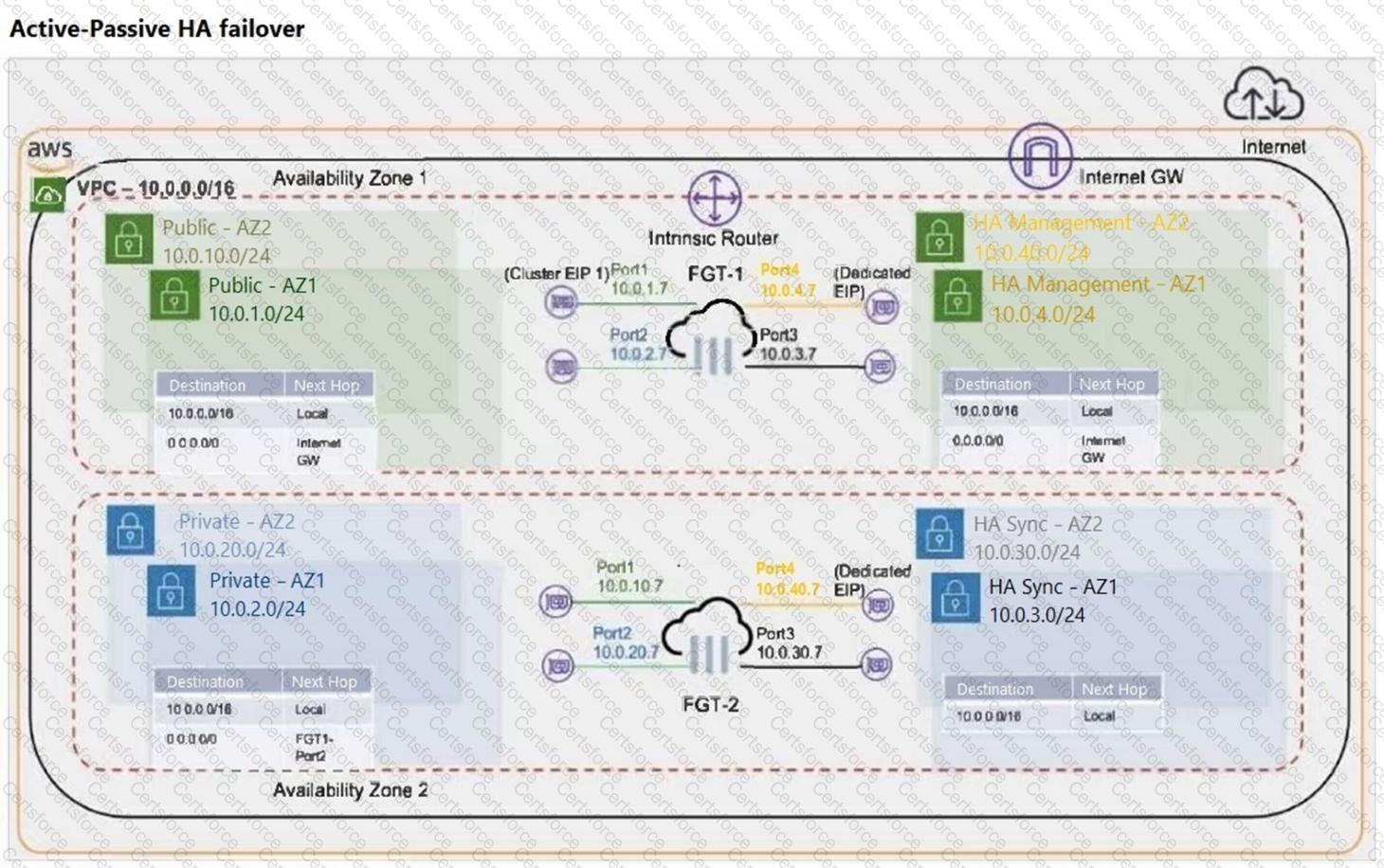
What occurs during a failover for an active-passive (A-P) cluster that is deployed in two different availability zones? (Choose two.)
Which three statements correctly describe FortiGate Cloud-Native Firewall (CNF)? (Choose three.)
You need to deploy a new Windows server in AWS to offload web traffic from an existing web server in a different availability zone.
According to the AWS shared responsibility model, what three actions must you take to secure the new EC2 instance? (Choose three.)