What is the expected behavior when enabling auto TX power control on a FortiAP interface?
Refer to the exhibit.
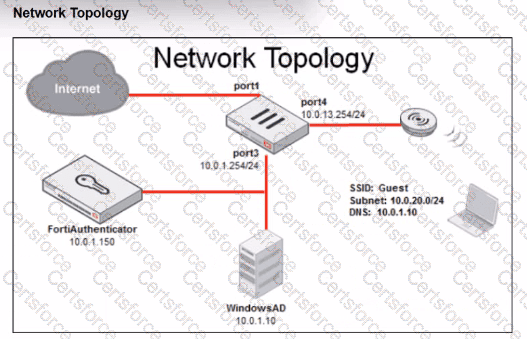
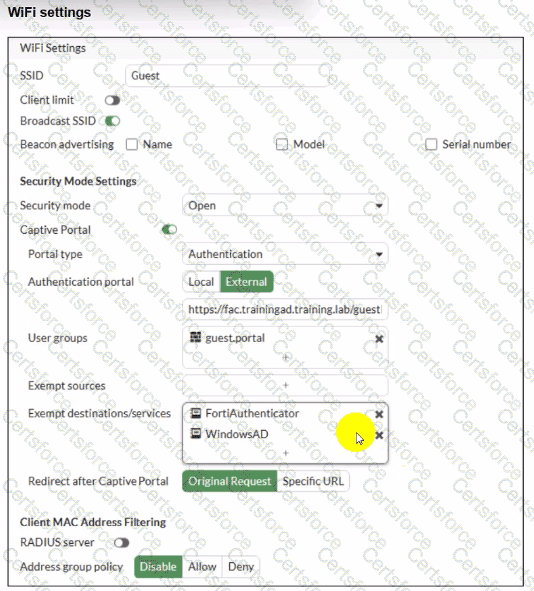
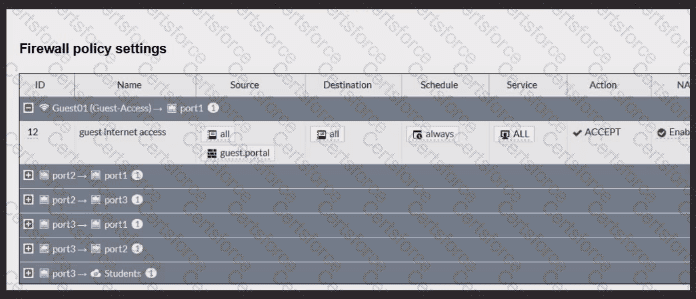
Review the exhibits to analyze the network topology, SSID settings, and firewall policies.
FortiGate is configured to use an external captive portal for authentication to grant access to a wireless network. During testing, it was found that users attempting to connect to the SSID cannot access the captive portal login page.
What configuration change should be made to resolve this issue to allow users to access the captive portal?
In a Windows environment using AD machine authentication, how does FortiAuthenticator ensure that a previously authenticated device is maintaining its network access once the device resumes operating after sleep or hibernation?
Which VLAN is used by FortiGate to place devices that fail to match any configured NAC policies? CRSPAN
APs have been manually configured to connect to FortiGate over an IPsec network, and FortiGate successfully detects and authorizes them. However, the APs remain unmanaged because FortiGate is unable to establish a CAPWAP tunnel with them.
What configuration change can resolve this issue and enable FortiGate to establish the CAPWAP tunnel over the IPsec connection?
Connectivity tests are being performed on a newly configured VLAN. The VLAN is configured on a FortiSwitch device that is managed by FortiGate. During testing, it is observed that devices
within the VLAN can successfully ping FortiGate. and FortiGate can also ping these devices.
Inter-VLAN communication is working as expected. However, devices within the same VLAN are unable to communicate with each other.
What could be causing this issue?
Refer to the exhibits.
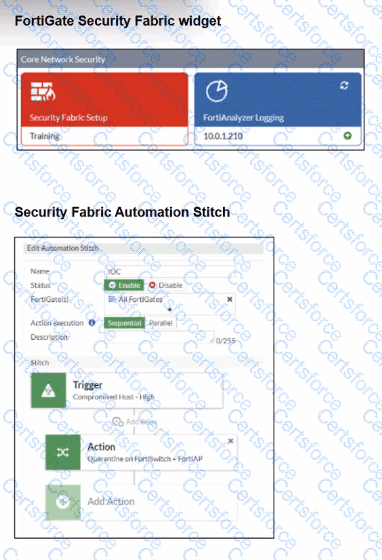
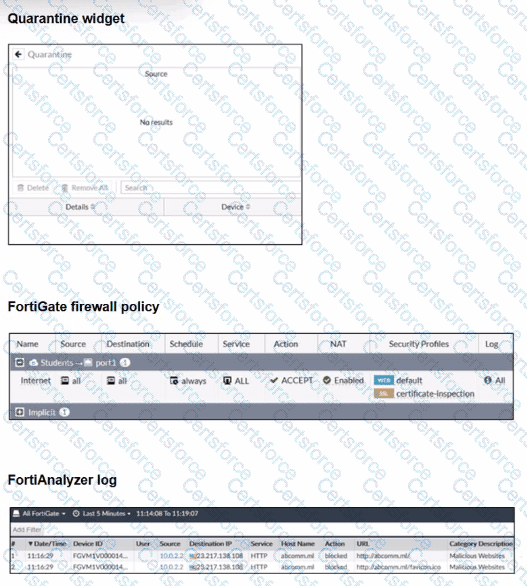
Examine the FortiGate configuration, FortiAnalyzer logs, and FortiGate widget shown in the exhibits.
Security Fabhc quarantine automation has been configured to isolate compromised devices automatically. FortiAnalyzer has been added to the Security Fabric, and an automation stitch has been configured to quarantine compromised devices.
To test the setup, a device with the IP address 10.0.2.1 that is connected through a managed FortiSwitch attempts to access a malicious website. The logs on FortiAnalyzer confirm that the event was recorded, but the device does not appear in the FortiGate quarantine widget.
Which two reasons could explain why FortiGate is not quarantining the device? (Choose two.)
You are configuring FortiAuthenticator to integrate with FSSO for user identification. To enable FortiAuthenticator to extract user information from syslog messages and inject it into FSSO, you have configured syslog matching rules.
What is the role of syslog matching rules in the process of injecting user information into FSSO?
You are deploying a FortiSwitch device managed by FortiGate in a secure network environment. To ensure accurate communication, you must identify which protocols are required for communication and control between FortiGate and FortiSwitch.
Which three protocols are used by FortiGate to manage and control FortiSwitch devices? (Choose three.)
You are setting up a captive portal to provide Wi-Fi access for visitors. To simplify the process, your team wants visitors to authenticate using their existing social media accounts instead of creating new accounts or entering credentials manually.
Which two actions are required to enable this functionality? (Choose two.)