A forensics investigator needs to copy data from a computer to some type of removable media so he can examine the information at another location. The problem is that the data is around 42GB in size. What type of removable media could the investigator use?
The use of warning banners helps a company avoid litigation by overcoming an employees assumed _________ when connecting to the company intranet, network, or virtual private network (VPN) and will allow the company investigators to monitor, search, and retrievecompany? intranet, network, or virtual private network (VPN) and will allow the company? investigators to monitor, search, and retrieve information stored within the network.
While looking through the IIS log file of a web server, you find the following entries:
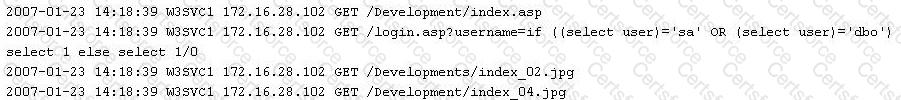
What is evident from this log file?
Microsoft Outlook maintains email messages in a proprietary format in what type of file?
You have been called in to help with an investigation of an alleged network intrusion. After questioning the members of the company ITYou have been called in to help with an investigation of an alleged network intrusion. After questioning the members of the company? IT department, you search through the server log files to find any trace of the intrusion. After that you decide to telnet into one of the company routers to see if there is any evidence to be found. While connected to the router, you see some unusual activity and believe that the attackers are currently connected to that router. You start up an ethereal session to begin capturing traffic on the router that could be used in the investigation. At what layer of the OSI model are you monitoring while watching traffic to and from the router?