Where is the default location for Apache access logs on a Linux computer?
When performing a forensics analysis, what device is used to prevent the system from recording data on an evidence disk?
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
During the course of a corporate investigation, you find that an employee is committing a federal crime. Can the employer file a criminal complain with the police?
You are working for a large clothing manufacturer as a computer forensics investigator and are called in to investigate an unusual case of an employee possibly stealing clothing designs from the company and selling them under a different brand name for a different company. What you discover during the course of the investigation is that the clothing designs are actually original products of the employee and the company has no policy against an employee selling his own designs on his own time. The only thing that you can find that the employee is doing wrong is that his clothing design incorporates the same graphic symbol as that of the company with only the wording in the graphic being different. What area of the law is the employee violating?
What encryption technology is used on Blackberry devices?Password Keeper?
Sniffers that place NICs in promiscuous mode work at what layer of the OSI model?
While presenting his case to the court, Simon calls many witnesses to the stand to testify. Simon decides to call Hillary Taft, a lay witness, to the stand. Since Hillary is a lay witness, what field would she be considered an expert in?
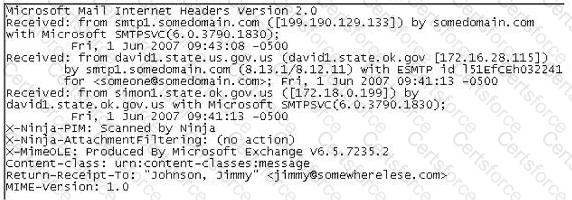
In the following email header, where did the email first originate from?
What is the name of the standard Linux command that can be used to create bit-stream images?