Cylie is investigating a network breach at a state organization in Florida. She discovers that the intruders were able to gain access into the company firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into thecompany? firewalls by overloading them with IP packets. Cylie then discovers through her investigation that the intruders hacked into the company phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the companycompany? phone system and used the hard drives on their PBX system to store shared music files. What would this attack on the company? PBX system be called?
You are assigned to work in the computer forensics lab of a state police agency. While working on a high profile criminal case, you have followed every applicable procedure, however your boss is still concerned that the defense attorney might question wheather evidence has been changed while at the lab. What can you do to prove that the evidence is the same as it was when it first entered the lab?
Where are files temporarily written in Unix when printing?
Chris has been called upon to investigate a hacking incident reported by one of his clients. The company suspects the involvement of an insider accomplice in the attack. Upon reaching the incident scene, Chris secures the physical area, records the scene using visual media. He shuts the system down by pulling the power plug so that he does not disturb the system in any way. He labels all cables and connectors prior to disconnecting any. What do you think would be the next sequence of events?
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
When investigating a wireless attack, what information can be obtained from the DHCP logs?
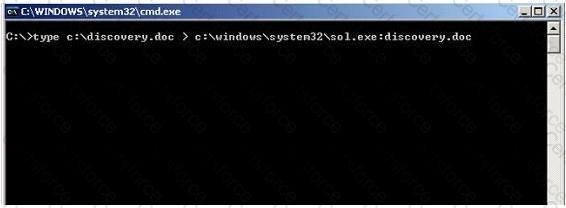
What feature of Windows is the following command trying to utilize?
What type of analysis helps to identify the time and sequence of events in an investigation?
The newer Macintosh Operating System (MacOS X) is based on:
Sectors in hard disks typically contain how many bytes?