A security administrator recently reset local passwords and the following values were recorded in the system:
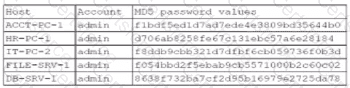
Which of the following in the security administrator most likely protecting against?
An engineer has ensured that the switches are using the latest OS, the servers have the latest patches, and the endpoints' definitions are up to date. Which of the following will these actions most effectively prevent?
Which of the following is prevented by proper data sanitization?
A company wants to verify that the software the company is deploying came from the vendor the company purchased the software from. Which of the following is the best way for the company to confirm this information?
A company wants to track modifications to the code used to build new virtual servers. Which of the following will the company most likely deploy?
Which of the following describes the procedures a penetration tester must follow while conducting a test?
Which of the following elements of digital forensics should a company use If It needs to ensure the integrity of evidence?
Which of the following would most likely be deployed to obtain and analyze attacker activity and techniques?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks.
Which of the following analysis elements did the company most likely use in making this decision?
An organization implemented cloud-managed IP cameras to monitor building entry points and sensitive areas. The service provider enables direct TCP/IP connection to stream live video footage from each camera. The organization wants to ensure this stream is encrypted and authenticated. Which of the following protocols should be implemented to best meet this objective?
A network manager wants to protect the company's VPN by implementing multifactor authentication that uses:
. Something you know
. Something you have
. Something you are
Which of the following would accomplish the manager's goal?
A security architect wants to prevent employees from receiving malicious attachments by email. Which of the following functions should the chosen solution do?
Which of the following methods to secure credit card data is best to use when a requirement is to see only the last four numbers on a credit card?
A data administrator is configuring authentication for a SaaS application and would like to reduce the number of credentials employees need to maintain. The company prefers to use domain credentials to access new SaaS applications. Which of the following methods would allow this functionality?
A company wants to improve the availability of its application with a solution that requires minimal effort in the event a server needs to be replaced or added. Which of the following would be the best solution to meet these objectives?