A technician wants to improve the situational and environmental awareness of existing users as they transition from remote to in-office work. Which of the following is the best option?
A security analyst is reviewing logs and discovers the following:

Which of the following should be used lo best mitigate this type of attack?
Which of the following would be the best way to test resiliency in the event of a primary power failure?
Which of the following cryptographic solutions protects data at rest?
While investigating a possible incident, a security analyst discovers the following log entries:
67.118.34.157 ----- [28/Jul/2022:10:26:59 -0300] "GET /query.php?q-wireless%20headphones / HTTP/1.0" 200 12737
132.18.222.103 ----[28/Jul/2022:10:27:10 -0300] "GET /query.php?q=123 INSERT INTO users VALUES('temp', 'pass123')# / HTTP/1.0" 200 935
12.45.101.121 ----- [28/Jul/2022:10:27:22 -0300] "GET /query.php?q=mp3%20players I HTTP/1.0" 200 14650
Which of the following should the analyst do first?
Which of the following provides the details about the terms of a test with a third-party penetration tester?
Which of the following security concepts is accomplished when granting access after an individual has logged into a computer network?
An analyst identifies that multiple users have the same passwords, but the hashes appear to be completely different. Which of the following most likely explains this issue?
Which of the following should be used to aggregate log data in order to create alerts and detect anomalous activity?
Which of the following makes Infrastructure as Code (IaC) a preferred security architecture over traditional infrastructure models?
A customer has a contract with a CSP and wants to identify which controls should be implemented in the IaaS enclave. Which of the following is most likely to contain this information?
An enterprise has been experiencing attacks focused on exploiting vulnerabilities in older browser versions with well-known exploits. Which of the following security solutions should be configured to best provide the ability to monitor and block these known signature-based attacks?
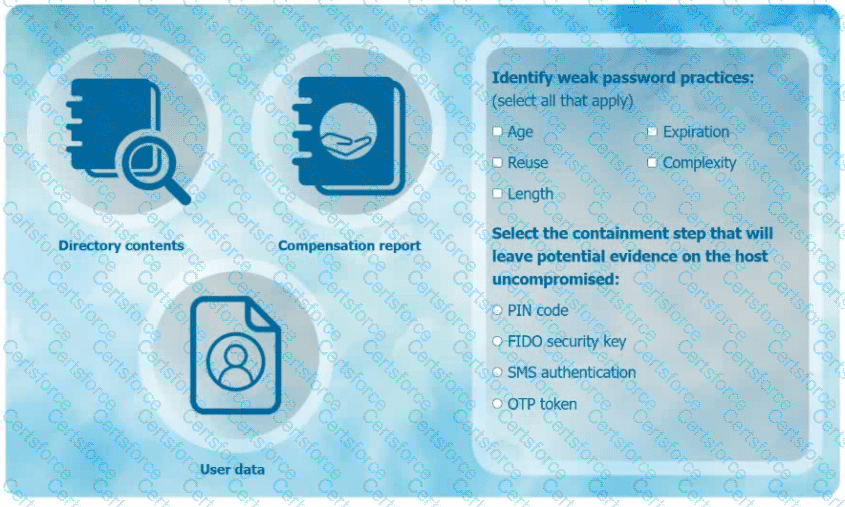
An organization has learned that its data is being exchanged on the dark web. The CIO
has requested that you investigate and implement the most secure solution to protect employee accounts.
INSTRUCTIONS
Review the data to identify weak security practices and provide the most appropriate
security solution to meet the CIO's requirements.
Sine© a recent upgrade (o a WLAN infrastructure, several mobile users have been unable to access the internet from the lobby. The networking team performs a heat map survey of the building and finds several WAPs in the area. The WAPs are using similar frequencies with high power settings. Which of the following installation considerations should the security team evaluate next?
Which of the following actions could a security engineer take to ensure workstations and servers are properly monitored for unauthorized changes and software?