A penetration tester wants to use multiple TTPs to assess the reactions (alerted, blocked, and others) by the client’s current security tools. The threat-modeling team indicates the TTPs in the list might affect their internal systems and servers. Which of the following actions would the tester most likely take?
An external legal firm is conducting a penetration test of a large corporation. Which of the following would be most appropriate for the legal firm to use in the subject line of a weekly email update?
A penetration testing team wants to conduct DNS lookups for a set of targets provided by the client. The team crafts a Bash script for this task. However, they find a minor error in one line of the script:
1 #!/bin/bash
2 for i in $(cat example.txt); do
3 curl $i
4 done
Which of the following changes should the team make to line 3 of the script?
A penetration tester wants to use PowerView in an AD environment. Which of the following is the most likely reason?
A penetration tester needs to identify all vulnerable input fields on a customer website. Which of the following tools would be best suited to complete this request?
During an engagement, a penetration tester runs the following command against the host system:
host -t axfr domain.com dnsl.domain.com
Which of the following techniques best describes what the tester is doing?
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
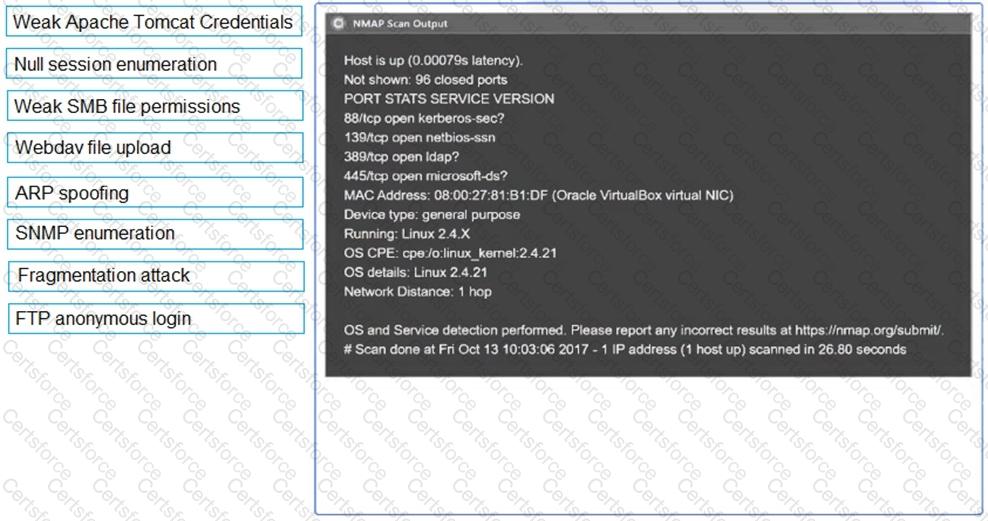
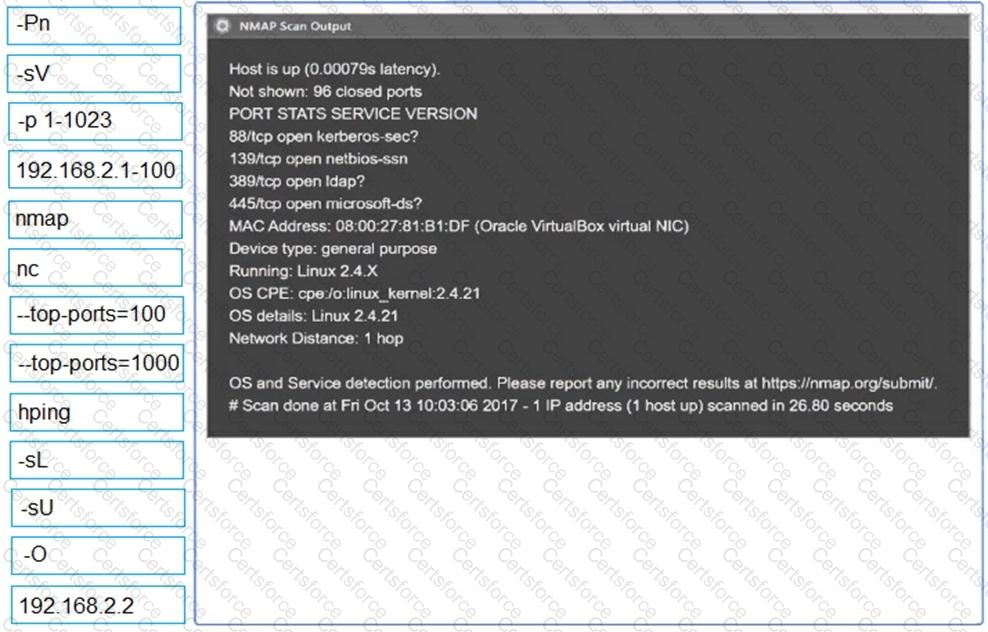
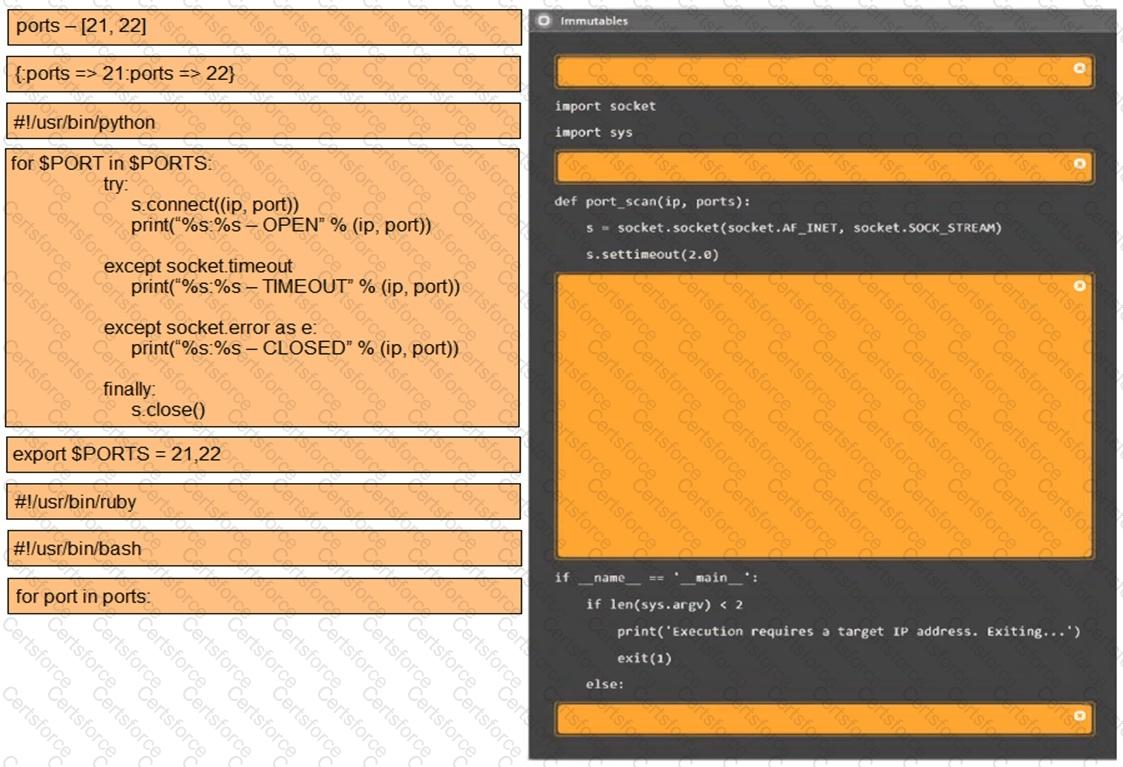
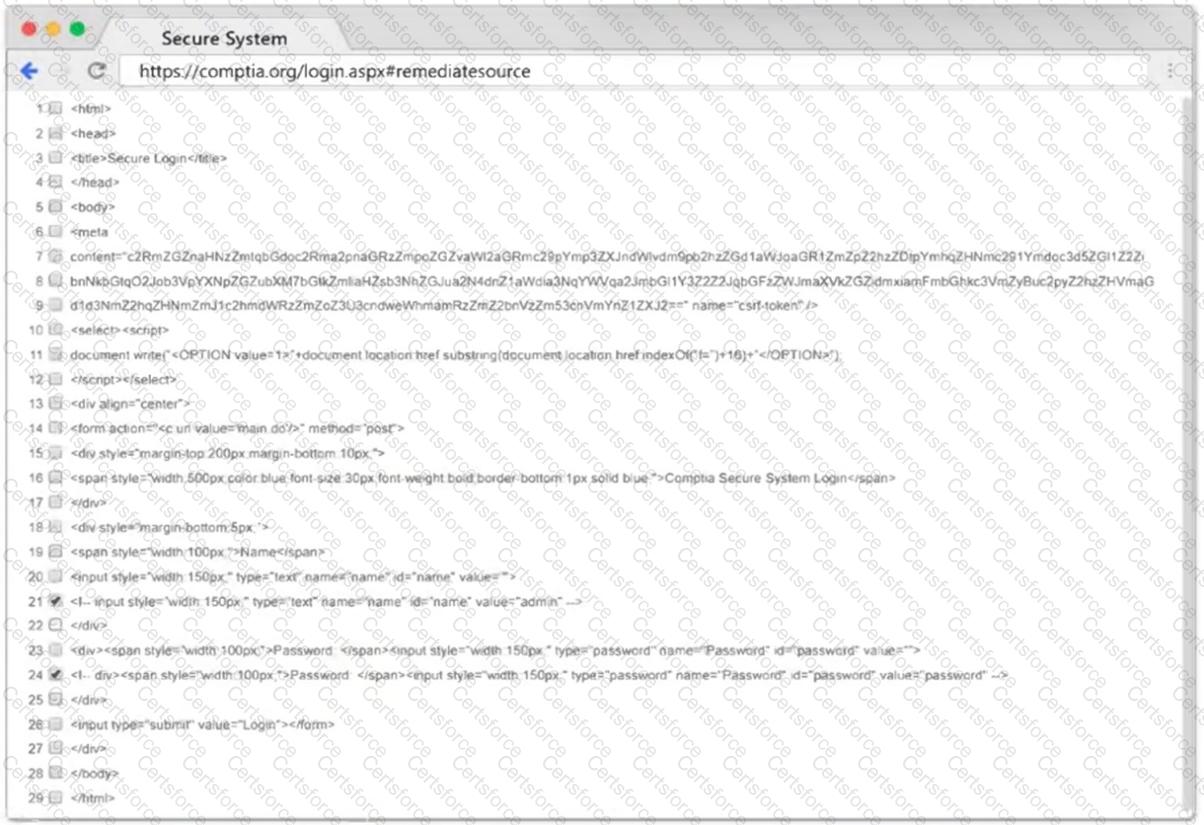

A penetration tester finds that an application responds with the contents of the /etc/passwd file when the following payload is sent:
<!DOCTYPE data [ ]>
Which of the following should the tester recommend in the report to best prevent this type of vulnerability?
During a security assessment, a penetration tester captures plaintext login credentials on the communication between a user and an authentication system. The tester wants to use this information for further unauthorized access.
Which of the following tools is the tester using?