During a penetration test, the tester uses a vulnerability scanner to collect information about any possible vulnerabilities that could be used to compromise the network. The tester receives the results and then executes the following command:
snmpwalk -v 2c -c public 192.168.1.23
Which of the following is the tester trying to do based on the command they used?
During a red-team exercise, a penetration tester obtains an employee's access badge. The tester uses the badge's information to create a duplicate for unauthorized entry. Which of the following best describes this action?
A company's incident response team determines that a breach occurred because a penetration tester left a web shell. Which of the following should the penetration tester have done after the engagement?
A penetration tester is evaluating a SCADA system. The tester receives local access to a workstation that is running a single application. While navigating through the application, the tester opens a terminal window and gains access to the underlying operating system. Which of the following attacks is the tester performing?
You are a penetration tester reviewing a client’s website through a web browser.
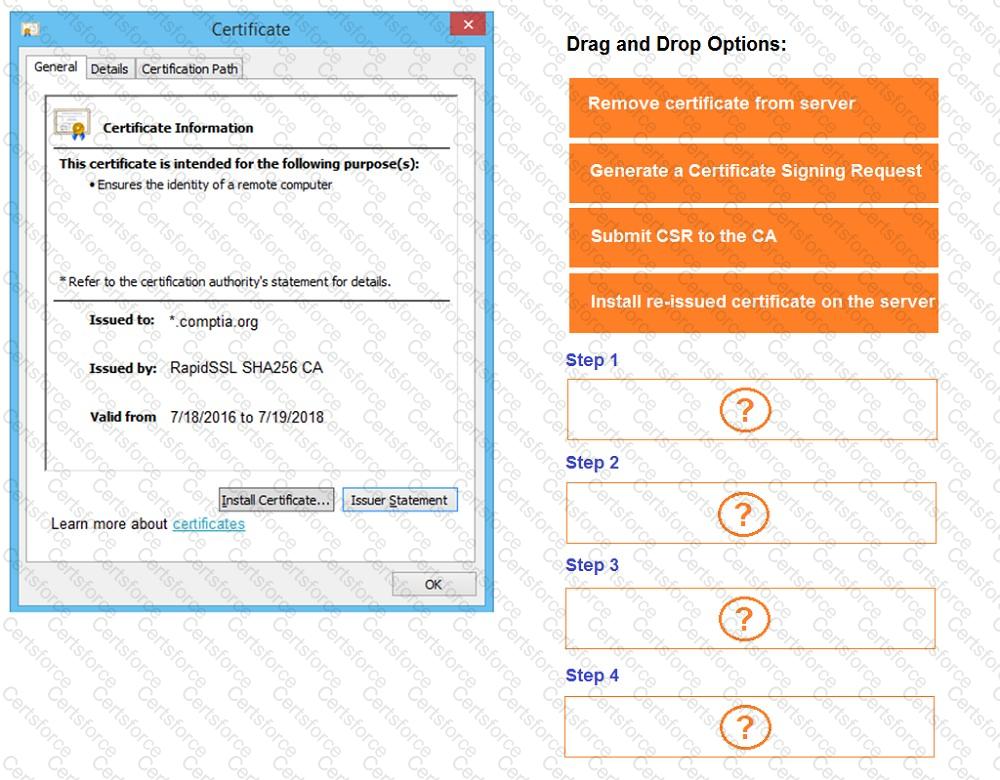
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
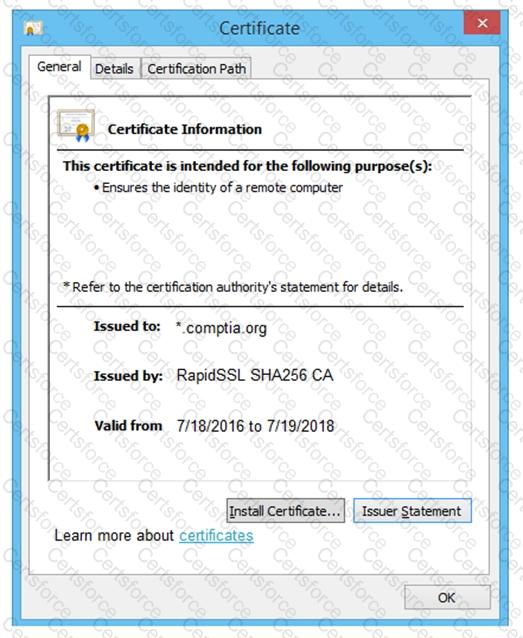

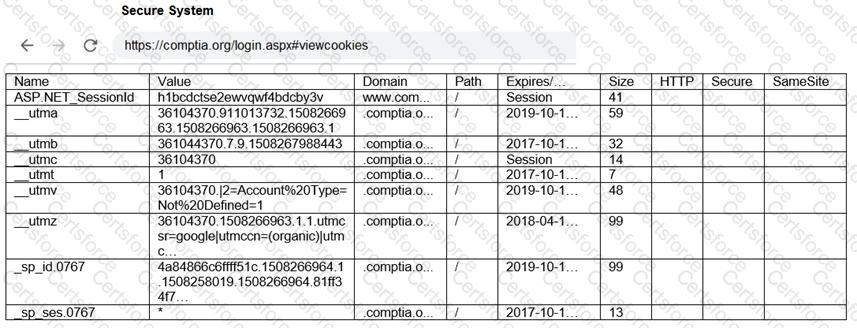

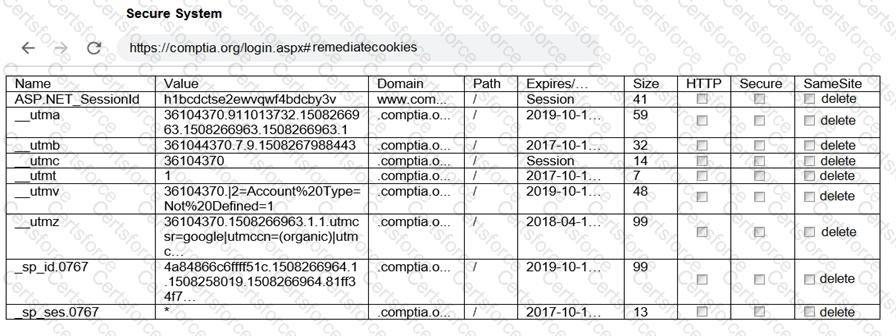
Which of the following OT protocols sends information in cleartext?
A penetration tester needs to scan a remote infrastructure with Nmap. The tester issues the following command:
nmap 10.10.1.0/24
Which of the following is the number of TCP ports that will be scanned?
While conducting a peer review for a recent assessment, a penetration tester finds the debugging mode is still enabled for the production system. Which of the following is most likely responsible for this observation?
A tester performs a vulnerability scan and identifies several outdated libraries used within the customer SaaS product offering. Which of the following types of scans did the tester use to identify the libraries?
A penetration tester is preparing a password-spraying attack against a known list of users for the company "example". The tester is using the following list of commands:
pw-inspector -i sailwords -t 8 -S pass
spray365.py spray -ep plan
users="~/user.txt"; allwords="~/words.txt"; pass="~/passwords.txt"; plan="~/spray.plan"
spray365.py generate --password-file $pass --userfile $user --domain "example.com" --execution-plan $plan
cew -m 5 "http://www.example.com " -w sailwords
Which of the following is the correct order for the list of the commands?