A penetration tester is working on a security assessment of a mobile application that was developed in-house for local use by a hospital. The hospital and its customers are very concerned about disclosure of information. Which of the following tasks should the penetration tester do first?
A penetration tester runs a network scan but has some issues accurately enumerating the vulnerabilities due to the following error:
OS identification failed
Which of the following is most likely causing this error?
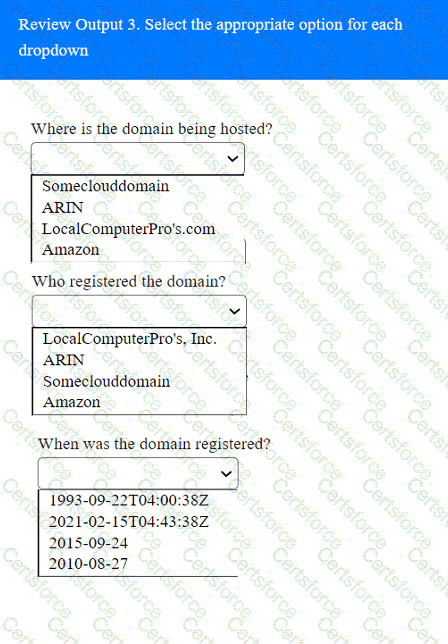
A penetration tester has been provided with only the public domain name and must enumerate additional information for the public-facing assets.
INSTRUCTIONS
Select the appropriate answer(s), given the output from each section.
Output 1
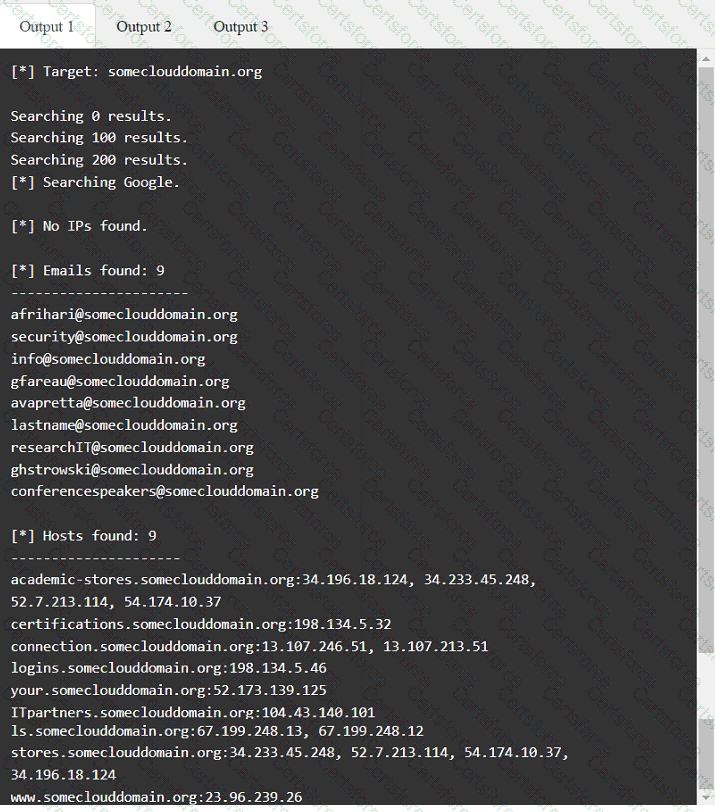
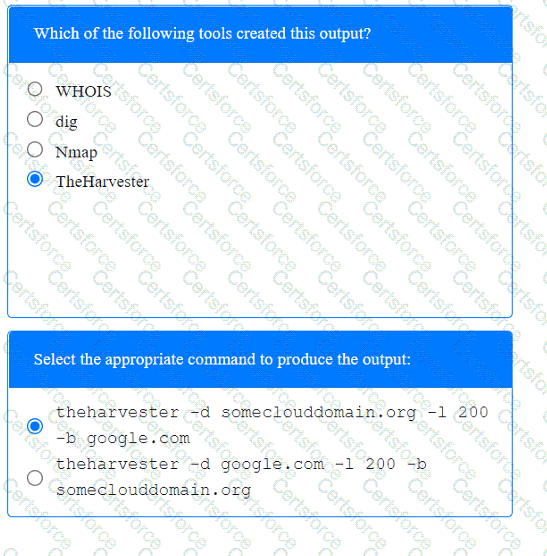
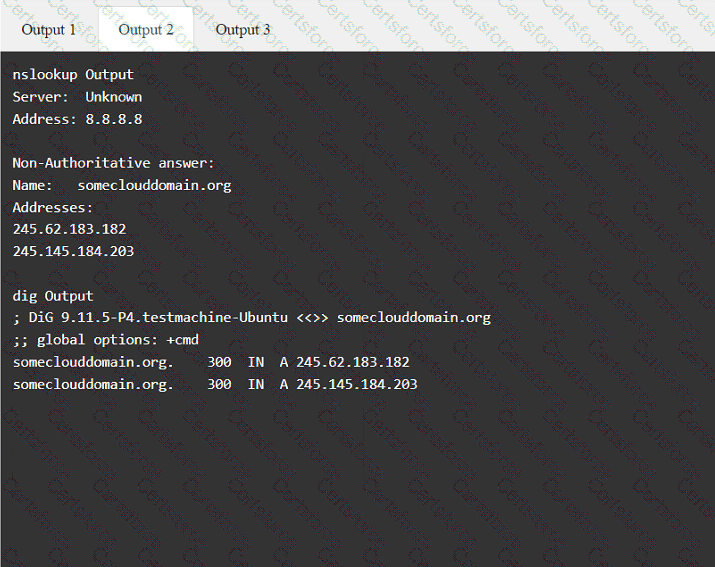
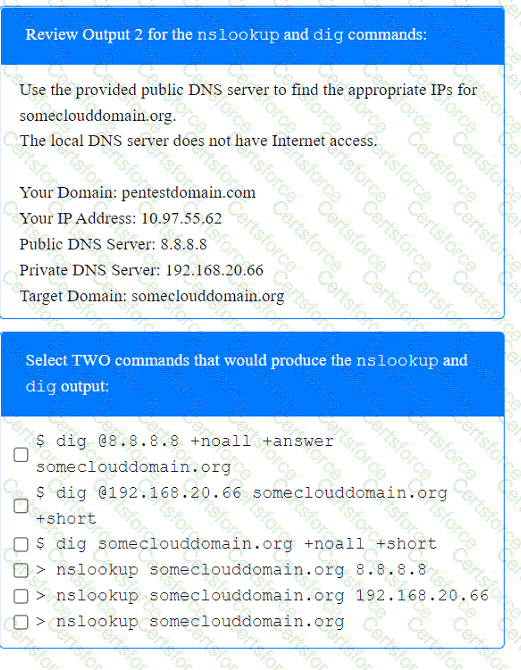

A tester is performing an external phishing assessment on the top executives at a company. Two-factor authentication is enabled on the executives’ accounts that are in the scope of work. Which of the following should the tester do to get access to these accounts?
A penetration tester is developing the rules of engagement for a potential client. Which of the following would most likely be a function of the rules of engagement?
A penetration tester completes a scan and sees the following Nmap output on a host:
Nmap scan report for victim (10.10.10.10)
Host is up (0.0001s latency)
PORT STATE SERVICE
161/udp open snmp
445/tcp open microsoft-ds
3389/tcp open ms-wbt-server
Running Microsoft Windows 7
OS CPE: cpe:/o:microsoft:windows_7::sp0
The tester wants to obtain shell access. Which of the following related exploits should the tester try first?
During a pre-engagement activity with a new customer, a penetration tester looks for assets to test. Which of the following is an example of a target that can be used for testing?
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
A penetration tester successfully gained access to manage resources and services within the company's cloud environment. This was achieved by exploiting poorly secured administrative credentials that had extensive permissions across the network. Which of the following credentials was the tester able to obtain?