A previous penetration test report identified a host with vulnerabilities that was
successfully exploited. Management has requested that an internal member of the
security team reassess the host to determine if the vulnerability still exists.
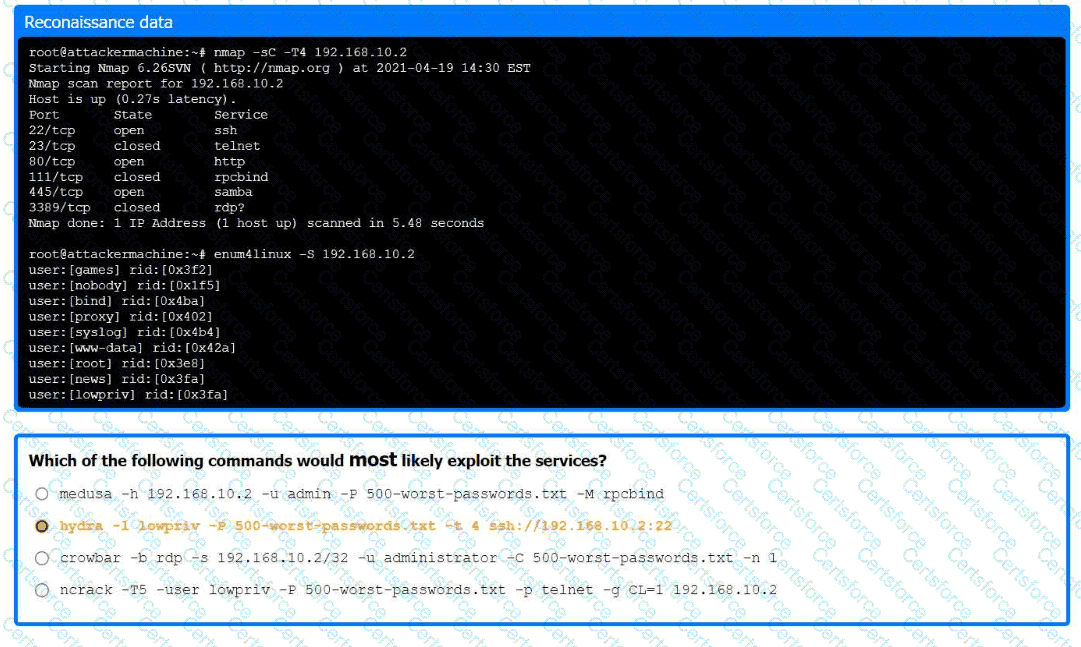
Part 1:
. Analyze the output and select the command to exploit the vulnerable service.
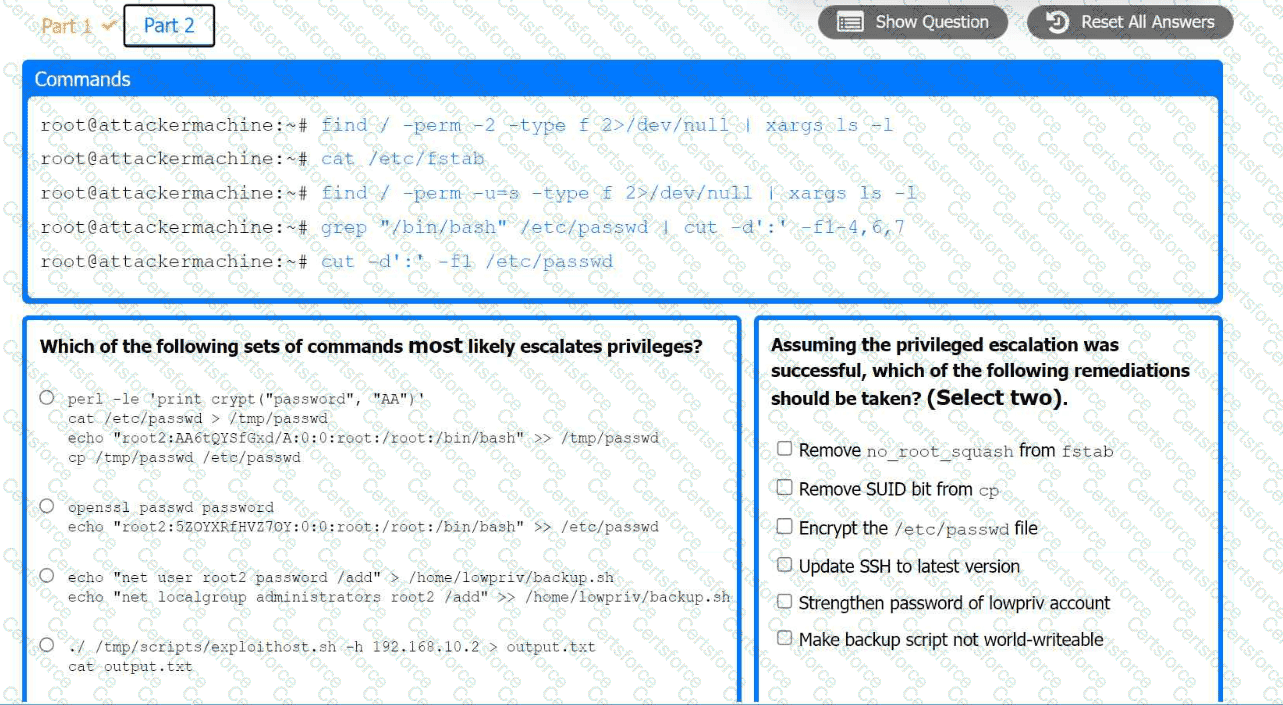
Part 2:
. Analyze the output from each command.
· Select the appropriate set of commands to escalate privileges.
· Identify which remediation steps should be taken.
A penetration tester plans to conduct reconnaissance during an engagement using readily available resources. Which of the following resources would most likely identify hardware and software being utilized by the client?
A penetration tester discovers data to stage and exfiltrate. The client has authorized movement to the tester's attacking hosts only. Which of the following would be most appropriate to avoid alerting the SOC?
During a penetration test, a tester compromises a Windows computer. The tester executes the following command and receives the following output:
mimikatz # privilege::debug
mimikatz # lsadump::cache
---Output---
lapsUser
27dh9128361tsg2€459210138754ij
---OutputEnd---
Which of the following best describes what the tester plans to do by executing the command?
A penetration testing team needs to determine whether it is possible to disrupt wireless communications for PCs deployed in the client’s offices. Which of the following techniques should the penetration tester leverage?
During a pre-engagement activity with a new customer, a penetration tester looks for assets to test. Which of the following is an example of a target that can be used for testing?
A penetration tester aims to exploit a vulnerability in a wireless network that lacks proper encryption. The lack of proper encryption allows malicious content to infiltrate the network. Which of the following techniques would most likely achieve the goal?
During an external penetration test, a tester receives the following output from a tool:
test.comptia.org
info.comptia.org
vpn.comptia.org
exam.comptia.org
Which of the following commands did the tester most likely run to get these results?
A penetration tester finds that an application responds with the contents of the /etc/passwd file when the following payload is sent:
<!DOCTYPE data [ ]>
Which of the following should the tester recommend in the report to best prevent this type of vulnerability?
A penetration tester wants to send a specific network packet with custom flags and sequence numbers to a vulnerable target. Which of the following should the tester use?