A web developer wants to ensure that malicious users can't type SQL statements when they asked for input, like their username/userid.
Which of the following query optimization techniques would effectively prevent SQL Injection attacks?
An analyst is reviewing the following data:
Car IDSpeed
123155
566436
564418
650567
546436
645638
Which of the following should the analyst include in the measures of central tendency for speed?
A company’s marketing department wants to do a promotional campaign next month. A data analyst on the team has been asked to perform customer segmentation, looking at how recently a customer bought the product, at what frequency, and at what value. Which of the following types of analysis would this practice be considered?
An analyst is building a new dashboard for a user. After an initial conversation with the user. the analyst created a mock-up of the dashboard. Which of the following best explains why the analyst created the mock-up?
Given the diagram below:
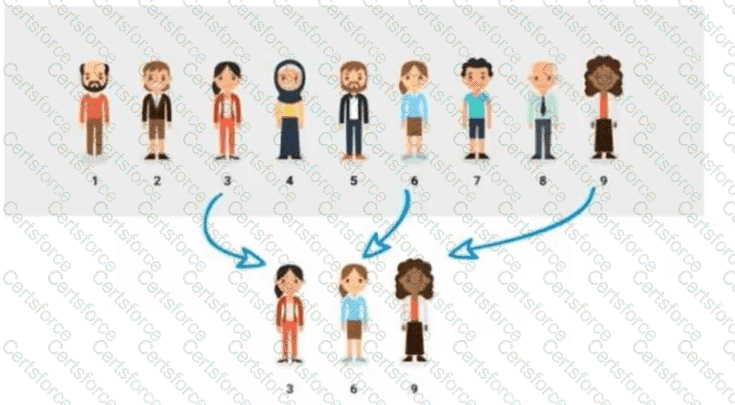
Which of the following types of sampling is depicted in the image?
Which of the following types of dashboards should a business intelligence engineer develop in order to provide information about failed data pipelines?
Which of the following defines the policies and procedures for managing the master data?
Exhibit.
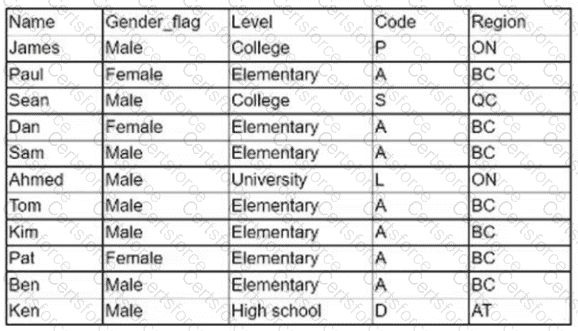
Which of the following logical statements results in Table B?
A)
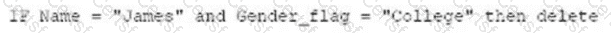
B)
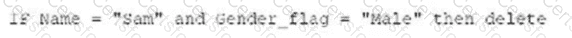
C)
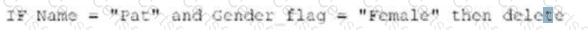
D)
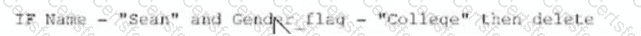
What would be an example of an acceptable form of primary identification for the Data+ exam?
Encryption is a mechanism for protecting data.
When should encryption be applied to data?
Choose the best answer.