Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
Which of the following is the focus of DevSecOps?
A security engineer recently discovered a vulnerability in the operating system of the company VMs. The operations team reviews the issue and decides all VMs need to be updated
from version 3.4.0 to 3.4.1. Which of the following best describes the type of update that will be applied?
A social networking company operates globally. Some users from Brazil and Argentina are reporting the following error: website address was not found. Which of the following is the most likely cause of this outage?
A security analyst reviews the daily logs and notices the following suspicious activity:
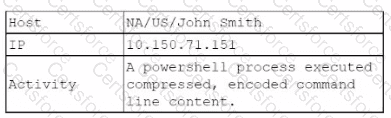
The analyst investigates the firewall logs and identities the following:
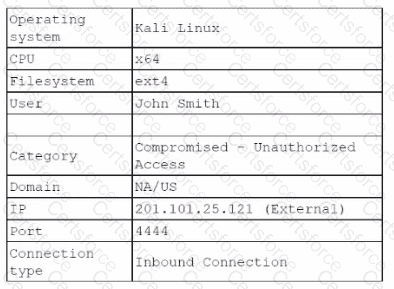
Which of the following steps should the security analyst take next to resolve this issue? (Select two).
Which of the following best describes why a project manager would decide to sign a fixed-price contract with a vendor?
A company has been using a CRM application that was developed in-house and is hosted on local servers. Due to internal changes, the company wants to migrate the application to the cloud without having to manage the infrastructure. Which of the following services should the company consider?
A cloud security analyst is investigating the impact of a recent cyberattack. The analyst is reviewing the following information:
Web server access log:
104.210.233.225 - - [21/10/2022:11:17: 40] "POST /uploadfile.html?f=myfile.php" 200 1638674
45.32.10.66 - - [21/10/2022:11:19:12] "GET /welcome.html" 200 5812
104.210.233.225 - - [21/10/2022:11:21:19] "GET / .. / .. / .. / .. /conf/server.xml HTTP/1.1" 200 74458
45.32.10.66 - - [21/10/22:11:22:32] "GET /admin.html HTTP/1.1" 200 9518
Web application firewall log:
"2022/10/21 11:17:33" "10.25.2.35" "104. 210.233.225" "userl" "File transfer completed successfully."
"2022/10/21 11:21:05" "10. 25.2. 35" "104. 210.233.225" "userl" "Accessed application page."
"2022/10/21 11:22:13" "10.25.2.35" "45. 32. 10. 66" "user2" "Accessing admin page. "
Which of the following has occurred?
A cloud engineer is extending on-premises services to a public cloud. The following design requirements must be considered in the overall solution:
" The ability to remotely connect systems from both environments
• No IP address conflicts or overlap
• Cost-effectiveness
Which of the following cloud network concepts best meets these requirements?
A project team is reviewing the project plan and related documents and identifies tasks that could be spread into smaller deliverables. Which of the following documents should the team edit first?