A security analyst reviews the daily logs and notices the following suspicious activity:
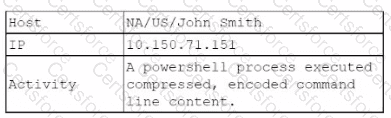
The analyst investigates the firewall logs and identities the following:
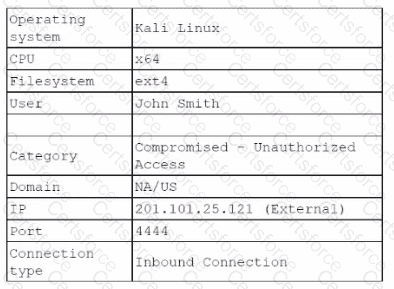
Which of the following steps should the security analyst take next to resolve this issue? (Select two).
Submit