A security analyst reviews a SIEM alert related to a suspicious email and wants to verify the authenticity of the message:
SPF = PASS
DKIM = FAIL
DMARC = FAIL
Which of the following did the analyst most likely discover?
An analyst is conducting monitoring against an authorized team that win perform adversarial techniques. The analyst interacts with the team twice per day to set the stage for the techniques to be used. Which of the following teams is the analyst a member of?
During security scanning, a security analyst regularly finds the same vulnerabilities in a critical application. Which of the following recommendations would best mitigate this problem if applied along the SDLC phase?
A Chief Information Security Officer has requested a dashboard to share critical vulnerability management goals with company leadership.
Which of the following would be the best to include in the dashboard?
A security analyst reviews a packet capture and identifies the following output as anomalous:
13:49:57.553161 TP10.203.10.17.45701>10.203.10.22.12930:Flags[FPU],seq108331482,win1024,urg0,length0
13:49:57.553162 IP10.203.10.17.45701>10.203.10.22.48968:Flags[FPU],seq108331482,win1024,urg0,length0
...
Which of the following activities explains the output?
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company:
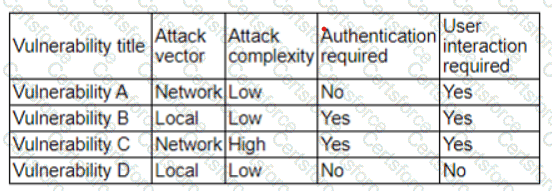
Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
An analyst needs to provide recommendations based on a recent vulnerability scan:
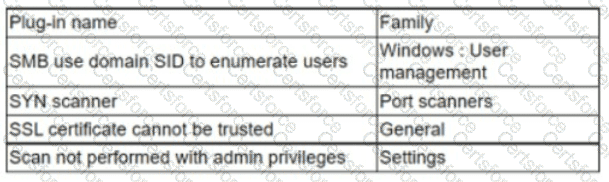
Which of the following should the analyst recommend addressing to ensure potential vulnerabilities are identified?
A systems administrator is reviewing after-hours traffic flows from data center servers and sees regular, outgoing HTTPS connections from one of the servers to a public IP address. The server should not be making outgoing connections after hours. Looking closer, the administrator sees this traffic pattern around the clock during work hours as well. Which of the following is the most likely explanation?
Which of the following documents sets requirements and metrics for a third-party response during an event?
Which of following would best mitigate the effects of a new ransomware attack that was not properly stopped by the company antivirus?