Which design benefit of PortFast is true?
SDN is still maturing. Throughout the evolution of SDN, which two things will play a key role in enabling a successful deployment and avoiding performance visibility gaps in the infrastructure? (Choose two.)
Which two conditions must be met for EIGRP to maintain an alternate loop-free path to a remote network? (Choose two.)
What are two advantages of controller-based networks versus traditional networks? (Choose two.)
An enterprise solution team is analyzing multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
While computer networks and sophisticated applications have allowed individuals to be more productive the need to prepare for security threats has increased dramatically A six-step methodology on security incident handling has been adopted by many organizations including service providers enterprises, and government organizations to ensure that organizations are aware of significant security incidents and act quickly to stop the attacker, minimize damage caused, and prevent follow on attacks or similar incidents in the future Drag and drop the actions on the left to the targets on the right in the correct order.
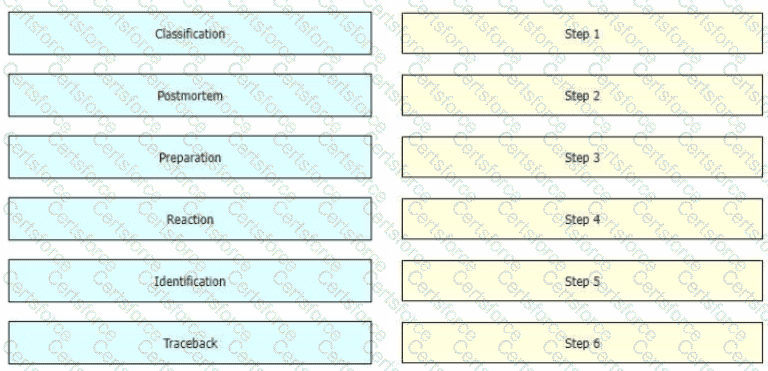
Refer to the exhibit.
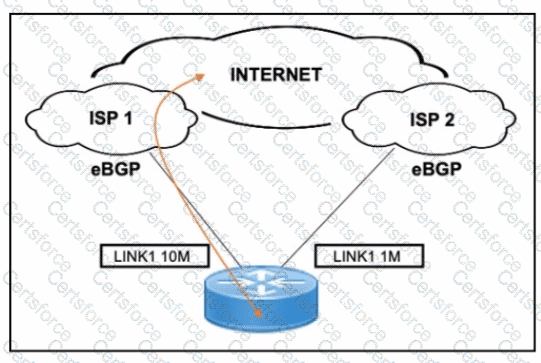
A customer has two eBGP internet links: one primary high-speed (10 Mbps) and one backup low-speed (1 Mbps). The requirement is to use the 10M link (ISP 1) for all inbound/outbound traffic and only use the 1M link (ISP 2) during failure.
What is the correct BGP-based design solution?
A European government passport agency considers upgrading its IT systems to increase performance and workload flexibility in response to constantly changing requirements. The budget manager wants to reduce capital expenses and IT staff and must adopt the lowest-cost technology. Which technology choice is suitable?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)