Company XYZ is designing the network for IPv6 security and they have these design requirements:
A switch or router must deny access to traffic from sources with addresses that are correct but topologically incorrect.
Devices must block Neighbor Discovery Protocol resolution for destination addresses not found in the binding table.
Which two IPv4 security features are recommended for this company? (Choose two)
Company XYZ is revisiting the security design for their data center because they now have a requirement to control traffic within a subnet and implement deep packet inspection. Which technology meets the updated requirements and can be incorporated into the design?
Refer to the exhibit.
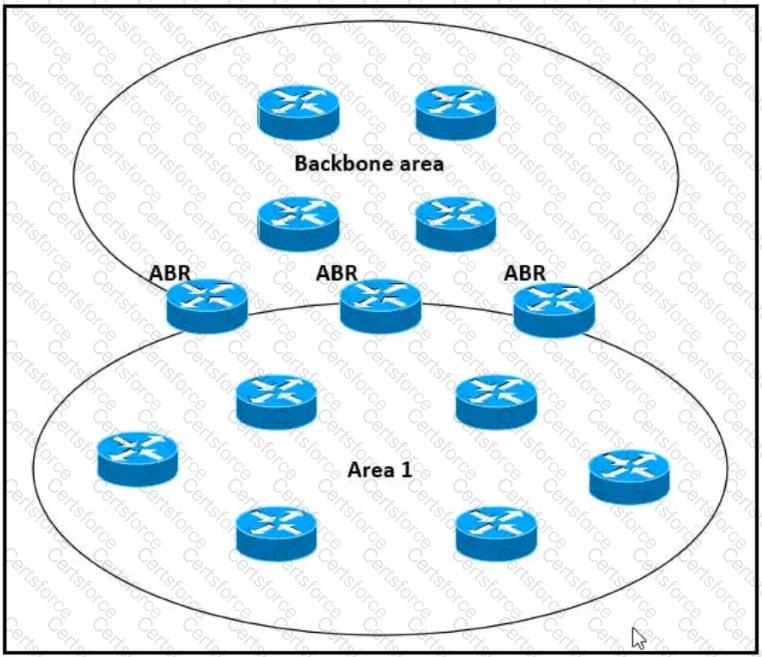
Which impact of using three or more ABRs between the backbone area and area 1 is true?
As part of workspace digitization, a large enterprise has migrated all their users to Desktop as a Service (DaaS), by hosting the backend system in their on-premises data center. Some of the branches have started to experience disconnections to the DaaS at periodic intervals, however, local users in the data center and head office do not experience this behavior. Which technology can be used to mitigate this issue?
Refer to the exhibit.
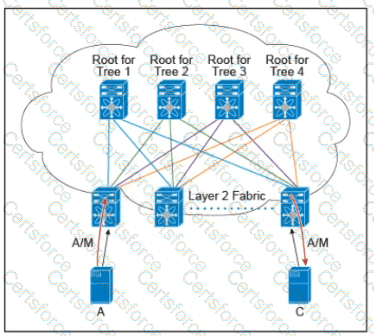
There are multiple trees in the Cisco FabricPath. All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two.)
Network changes due to mergers, acquisitions, and divestitures can be highly disruptive if not carefully planned. When an organization sells part of its business, it must detach those parts of the network with minimal risk and downtime.
Which network design approach is appropriate to minimize the impact and risks as the divested parts of the network are detached?
Refer to the exhibit.
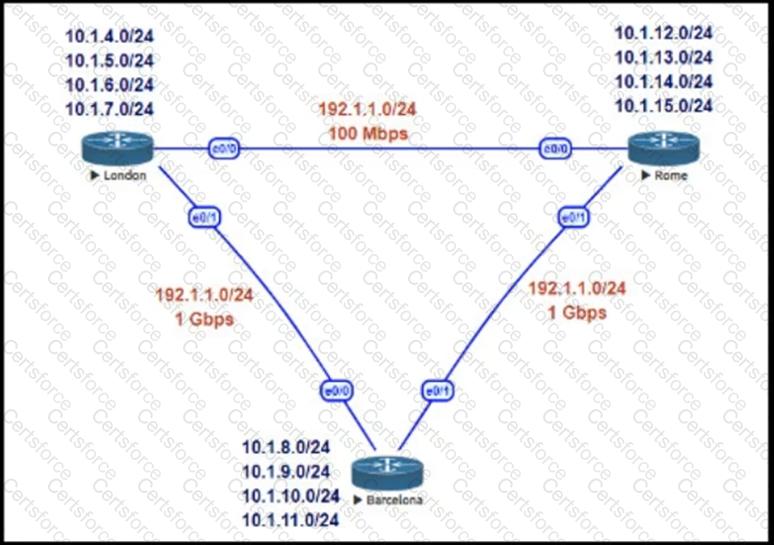
This network is running EIGRP as the routing protocol and the internal networks are being advertised in EIGRP. Based on the link speeds, all traffic between London and Rome is getting propagated via Barcelona and the direct link between London and Rome is not being utilized under normal working circumstances. The EIGRP design should allow for efficiency in the routing table by minimizing the routes being exchanged. The link between London and Rome should be utilized for specific routes. Which two steps accomplish this task? (Choose two.)
IPFIX data collection via standalone IPFIX probes is an alternative to flow collection from routers and switches. Which use case is suitable for using IPFIX probes?
Which service abstracts away the management of the operating system, middleware, and runtime?
Which two factors provide multifactor authentication for secure access to applications and data? (Choose two.)