Which three reasons to deploy an IDS sensor in promiscuous mode when you design a security solution are true? (Choose three.)
How must queue sizes be designed to ensure that an application functions correctly?
Refer to the exhibit.
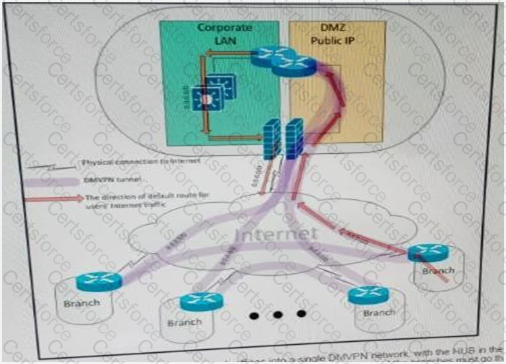
A customer interconnected hundreds of branch offices into a single DMVPN network, with the HUB in the main data center. Due to security policies, the customer requires that the default route for all Internet traffic from the users at the branches must go through the tunnel and the only connections that are allowed to and from the branch router over the local internet circuit are the DMVPN tunnels. Which two combined actions must you take on the branch router to address these security requirements and keep the solution scalable? (Choose two)
When is it required to leak routes into an IS-IS level 1 area?
Which option describes a design benefit of root guard?
A large enterprise network has two data centers and a WLAN edge with a large hub-and spoke network. The complete network is configured as a single OSPF area, and spoke routers are connected to unreliable WAN links. Which two changes should you make to deploy LSA on the spoke routers? (Choose two)
You are designing the QoS features for a large enterprise network that includes DMVPN. In which situation should you use the QoS pre-classify feature?
Refer to the exhibit.

How should you redesign this network running BGP to improve availability of the routers 1A and 1B at the core site?
As a part of a network design, you should tighten security to prevent man-in-the-middle. Which two security options ensure that authorized ARP responses take place according to know IP-to-MAC address mapping? (Choose two)
Refer to the exhibit.

In a link failure scenario, what is a benefit of adding APS protected link to the design solution?