What are two principles according to the build, release, run principle of the twelve-factor app methodology?
(Choose two.)
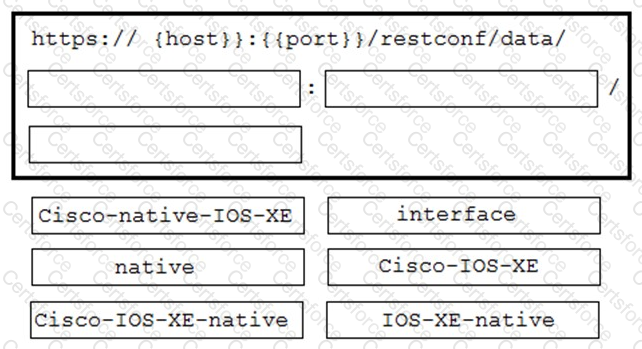
A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Drag and drop the
components from the bottom onto the box where the code is missing to complete the RESTCONF URI. Not all
options are used.
Refer to the exhibit.
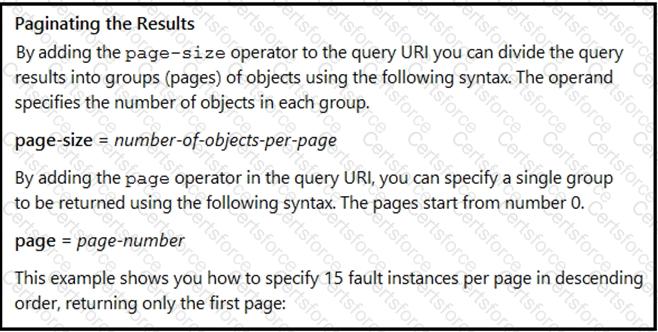
Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
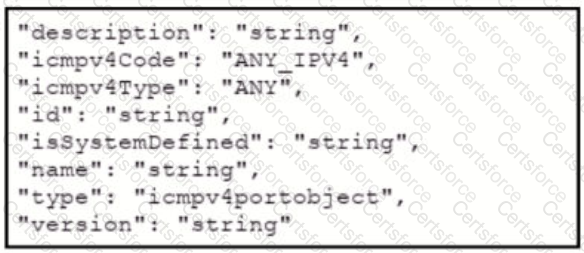
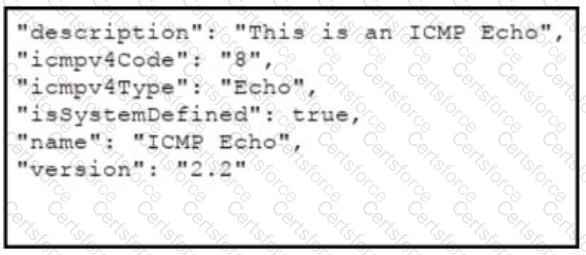
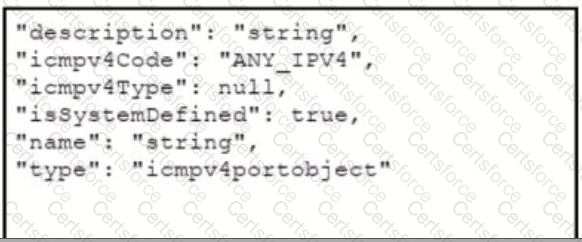
Refer to the exhibits which show the documentation associated with the create port object API cafl in Cisco Firepower Threat Defense, and a cURL command. Which data payload completes the cURL command to run the APi call?
A)
B)
C)
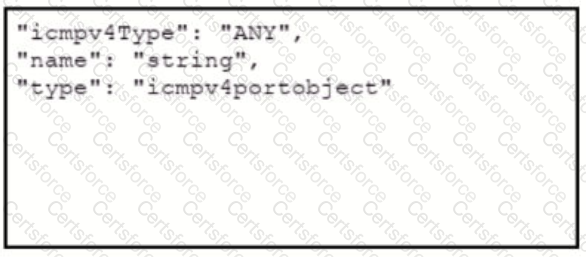
D)
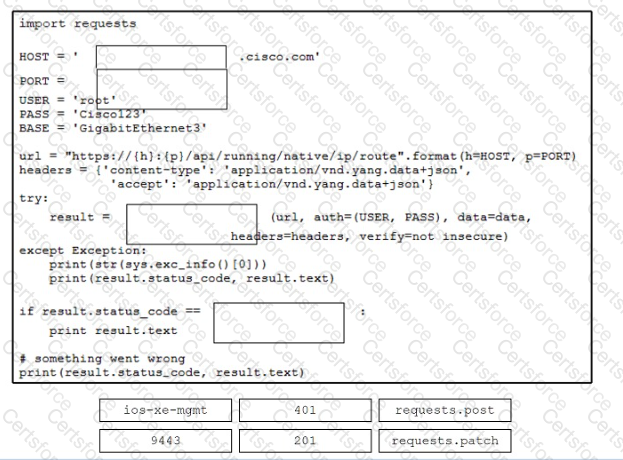
Drag and drop the code from the bottom onto the box where the code is missing to configure a router that runs Cisco IOS XE by using RESTCONF. The API call is made to the management URL of the IOS XE device and on a registered port number. Errors that are caught during HTTP operation are registered. Not all options are used.
A developer is designing a modem, distributed microservice enterprise application. The application will be integrating with other systems and focus on a large deployment, so control of API calls is necessary. What is the best practice to reduce application response latency and protect the application from excessive use?
DRAG DROP
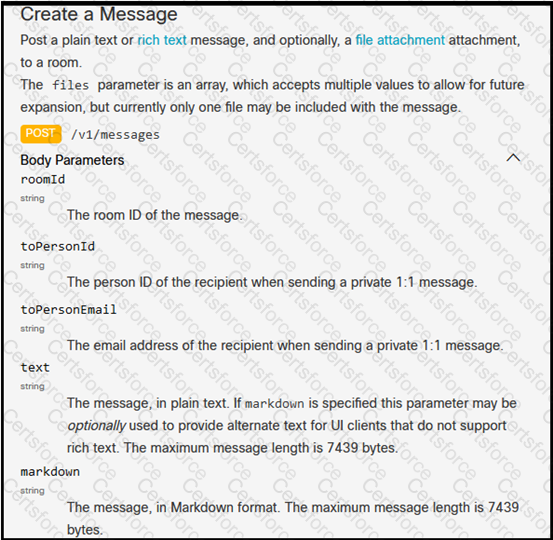
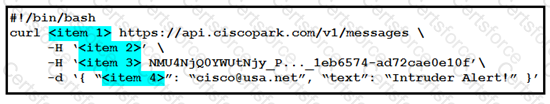
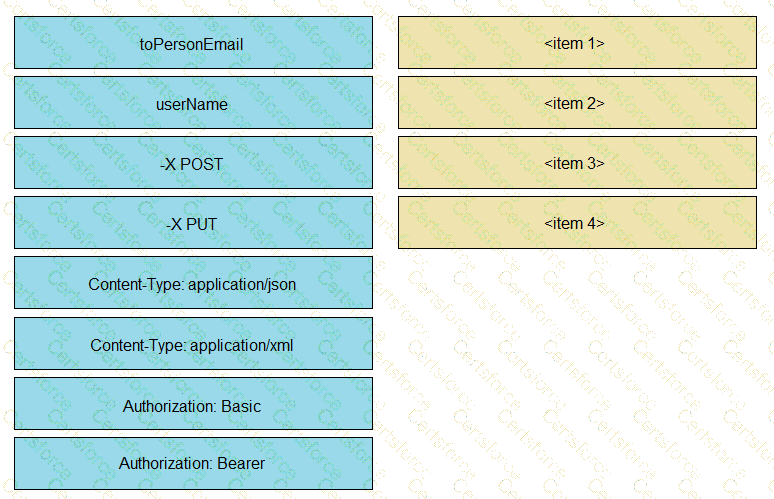
Refer to the exhibit. A system administrator has installed a Linux-based alarm system in their home that can execute a Bash shell script when an intruder is detected. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a chat-ops script that will notify of alarms via the Webex Teams REST API. Not all code snippets are used.
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
Refer to the exhibit.
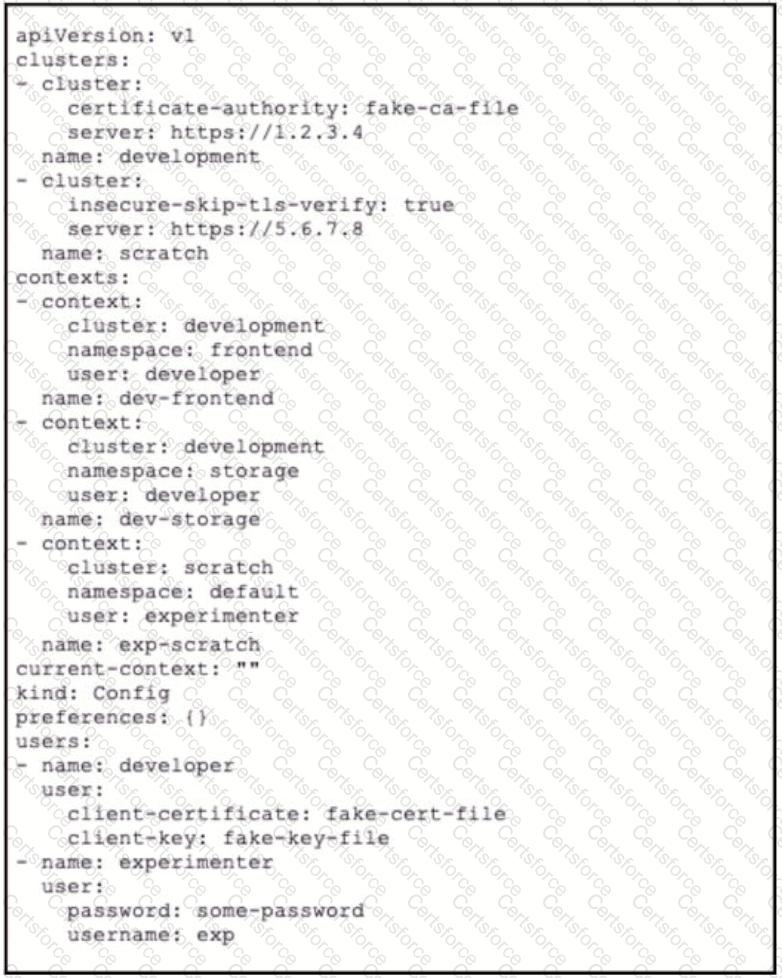
A kubeconfig file to manage access to Kubernetes clusters is shown. How many Kubernetes clusters are defined in the
file, and which cluster FS accessed using username/password authentication rather than using a certificate?
Which kind of API that is used with Cisco DNA Center provisions SSIDs, QoS policies, and update software versions on switches?